Question 151
Which action disables Zero Touch Provisioning (ZTP) functionality on a ZTP firewall during the onboarding process?
Question 152
Which protection feature is available only in a Zone Protection Profile?
Question 153
If the firewall is configured for credential phishing prevention using the "Domain Credential Filter" method, which login will be detected as credential theft?
Question 154
How can a candidate or running configuration be copied to a host external from Panorama?
Question 155
Refer to the exhibit.
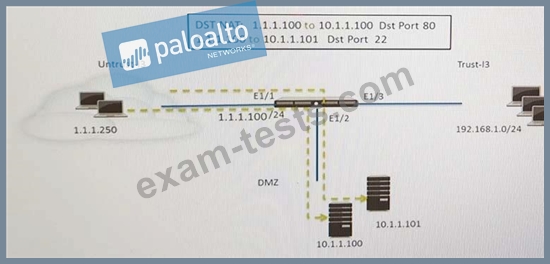
An administrator is using DNAT to map two servers to a single public IP address. Traffic will be steered to the specific server based on the application, where Host A (10.1.1.100) receives HTTP traffic and HOST B (10.1.1.101) receives SSH traffic.) Which two security policy rules will accomplish this configuration? (Choose two.)

An administrator is using DNAT to map two servers to a single public IP address. Traffic will be steered to the specific server based on the application, where Host A (10.1.1.100) receives HTTP traffic and HOST B (10.1.1.101) receives SSH traffic.) Which two security policy rules will accomplish this configuration? (Choose two.)

