Question 221
An administrator needs to evaluate a recent policy change that was committed and pushed to a firewall device group.
How should the administrator identify the configuration changes?
How should the administrator identify the configuration changes?
Question 222
An administrator sees several inbound sessions identified as unknown-tcp in the Traffic logs. The
administrator determines that these sessions are form external users accessing the company's proprietary
accounting application. The administrator wants to reliably identify this traffic as their accounting
application and to scan this traffic for threats.
Which option would achieve this result?
administrator determines that these sessions are form external users accessing the company's proprietary
accounting application. The administrator wants to reliably identify this traffic as their accounting
application and to scan this traffic for threats.
Which option would achieve this result?
Question 223
Which two methods can be used to verify firewall connectivity to AutoFocus? (Choose two.)
Question 224
A client has a sensitive application server in their data center and is particularly concerned about resource exhaustion because of distributed denial-of-service attacks.
How can the Palo Alto Networks NGFW be configured to specifically protect this server against resource exhaustion originating from multiple IP addresses (DDoS attack)?
How can the Palo Alto Networks NGFW be configured to specifically protect this server against resource exhaustion originating from multiple IP addresses (DDoS attack)?
Question 225
Click the Exhibit button below,
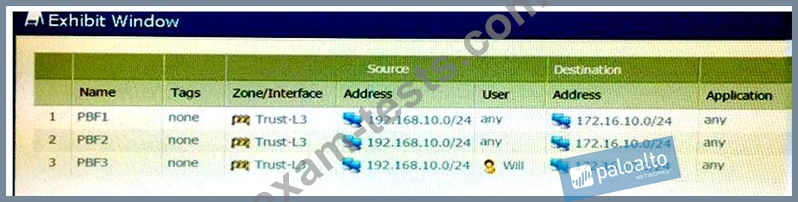
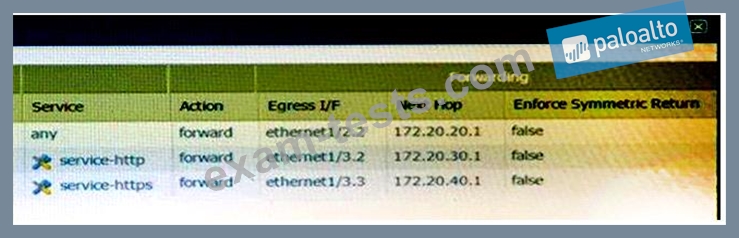
A firewall has three PBF rules and a default route with a next hop of 172.20.10.1 that is configured in the default VR. A user named Will has a PC with a 192.168.10.10 IP address. He makes an HTTPS connection to 172.16.10.20.
Which is the next hop IP address for the HTTPS traffic from Will's PC?


A firewall has three PBF rules and a default route with a next hop of 172.20.10.1 that is configured in the default VR. A user named Will has a PC with a 192.168.10.10 IP address. He makes an HTTPS connection to 172.16.10.20.
Which is the next hop IP address for the HTTPS traffic from Will's PC?

