Question 21
A company uses Microsoft 365. You are developing a model-driven app.
The app must meet the following requirements:
Use SharePoint Online for document storage.
Send emails by using Exchange Online.
You need to configure integrations.
What should you configure? To answer, drag the appropriate configuration options to the correct requirements. Each configuration option may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.
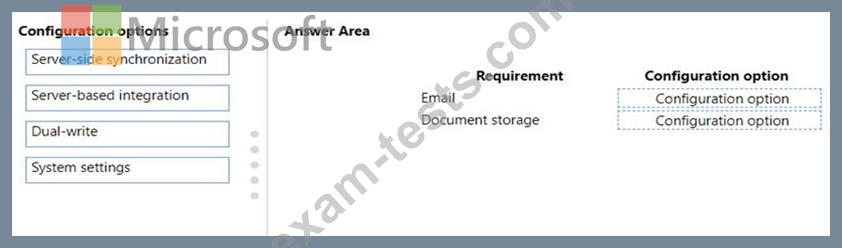
The app must meet the following requirements:
Use SharePoint Online for document storage.
Send emails by using Exchange Online.
You need to configure integrations.
What should you configure? To answer, drag the appropriate configuration options to the correct requirements. Each configuration option may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.

Question 22
A company has a Common Data Service (CDS) environment.
All accounts in the system with a relationship type of Customer set must have an account number. A plug-in has been developed.
When a Customer is updated with a relationship type, the plug-in sets the account number if not provided by the user.
You need to register the plug-in.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.

All accounts in the system with a relationship type of Customer set must have an account number. A plug-in has been developed.
When a Customer is updated with a relationship type, the plug-in sets the account number if not provided by the user.
You need to register the plug-in.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.

Question 23
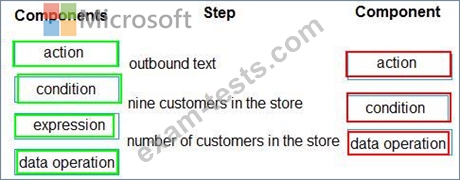
You need to identify why employees are not receiving notification that nine customers are checked in and waiting in the repair area.
Which components should you test for each step? To answer, drag the appropriate components to the correct steps. Each component may be used once, more than once, or not at all.
You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.
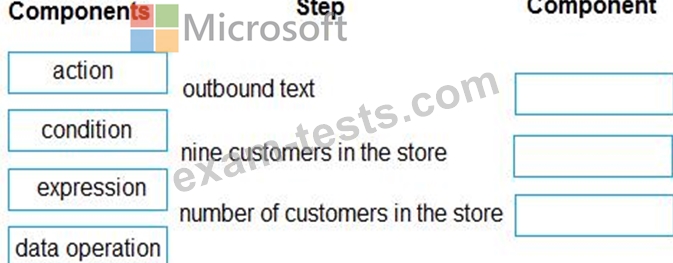
Which components should you test for each step? To answer, drag the appropriate components to the correct steps. Each component may be used once, more than once, or not at all.
You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.

Question 24
An organization has a Dynamics 365 Sales environment. In the development environment, you create a business rule named BusinessRule1 on the Account entity. You deploy BusinessRule1 to production as part of a managed solution.
You need to remove BusinessRule1 from the production environment.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.

You need to remove BusinessRule1 from the production environment.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.

Question 25
You need to set up security to meet the requirements.
How should you configure security? To answer, drag the appropriate security mechanisms to the correct users. Each security mechanism may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.
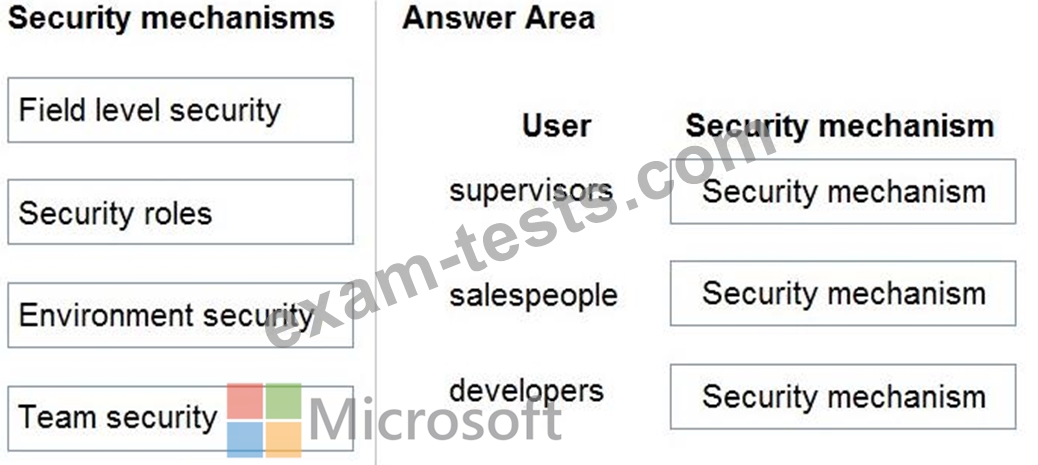
How should you configure security? To answer, drag the appropriate security mechanisms to the correct users. Each security mechanism may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.