Question 11
Which three signature-based Threat Prevention features of the firewall are informed by intelligence from the Threat Intelligence Cloud? (Choose three.)
Question 12
Which three script types can be analyzed in WildFire? (Choose three)
Question 13
Which two configuration elements can be used to prevent abuse of stolen credentials? (Choose two.)
Question 14
Which CLI allows you to view the names of SD-WAN policy rules that send traffic to the specified virtual SD-WAN interface, along with the performance metrics?
A)
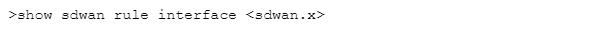
B)
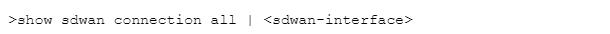
C)
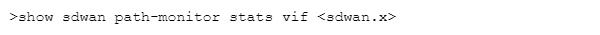
D)
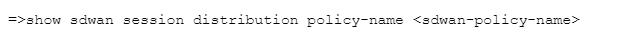
A)
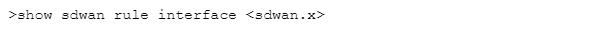
B)
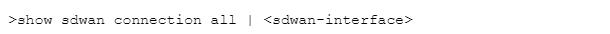
C)
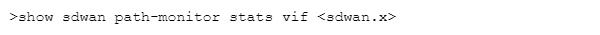
D)
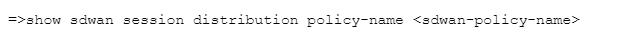
Question 15
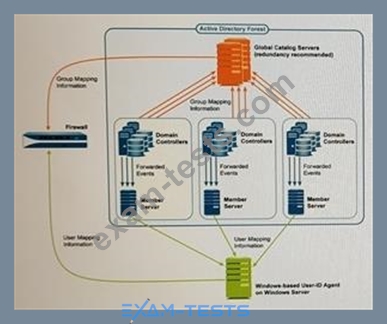
Given the following network diagram, an administrator is considering the use of Windows Log Forwarding and Global Catalog servers for User-ID implementation. What are two potential bandwidth and processing bottlenecks to consider? (Choose two.)