Question 81
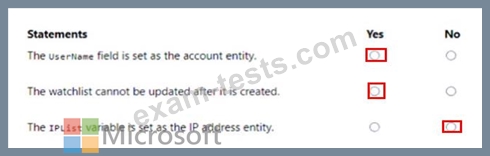
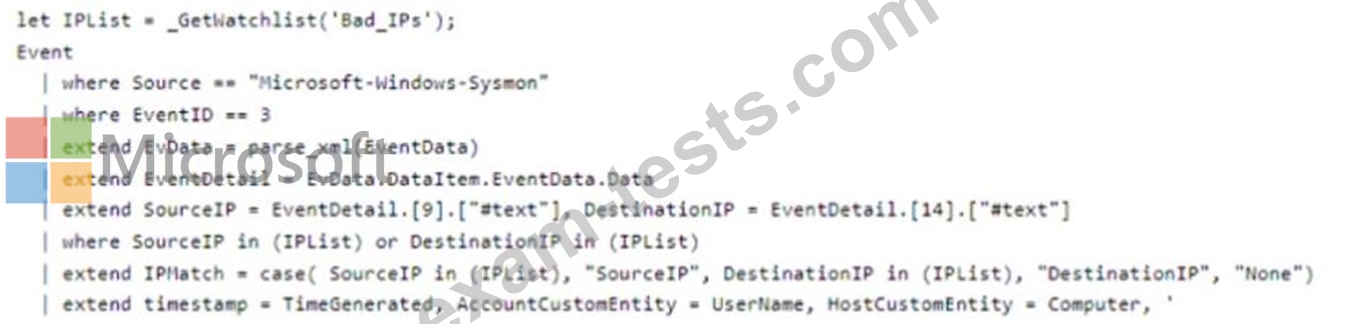
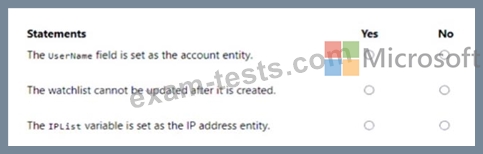
You have the following KQL query.


Question 82
You have a Microsoft 365 E5 subscription that contains 200 Windows 10 devices enrolled in Microsoft Defender for Endpoint.
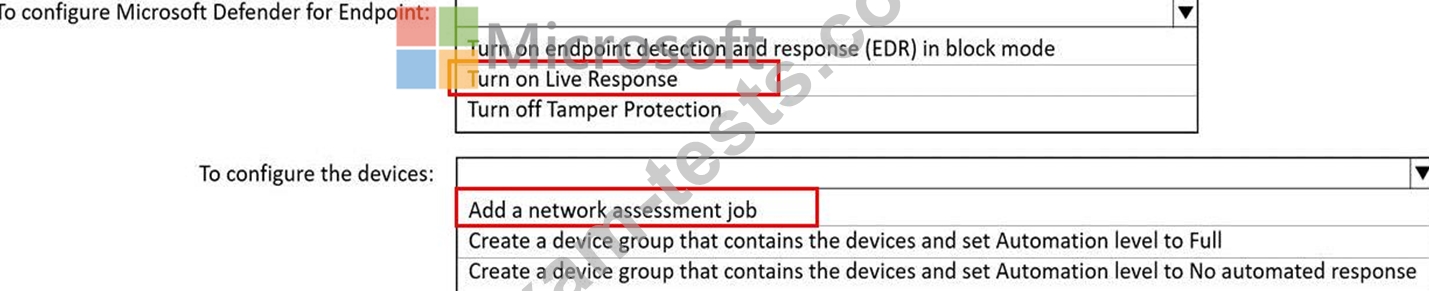
You need to ensure that users can access the devices by using a remote shell connection directly from the Microsoft 365 Defender portal. The solution must use the principle of least privilege.
What should you do in the Microsoft 365 Defender portal? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
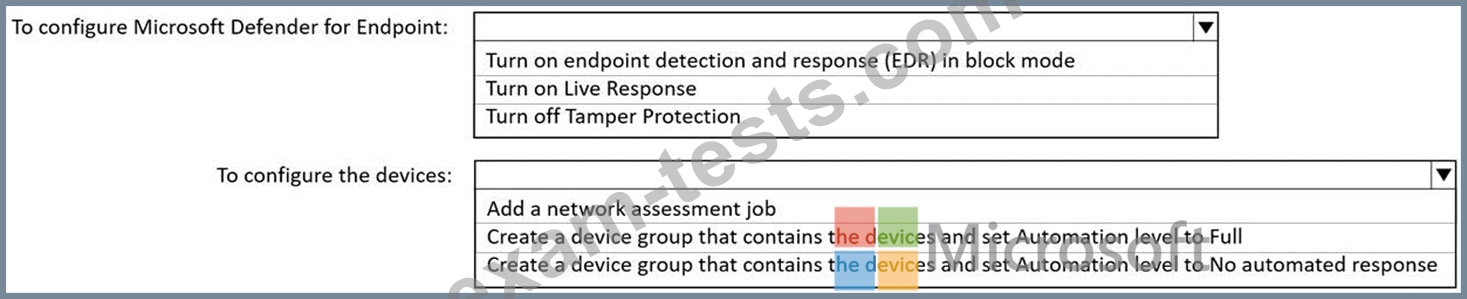
You need to ensure that users can access the devices by using a remote shell connection directly from the Microsoft 365 Defender portal. The solution must use the principle of least privilege.
What should you do in the Microsoft 365 Defender portal? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

Question 83
You have an Azure Storage account that will be accessed by multiple Azure Function apps during the development of an application.
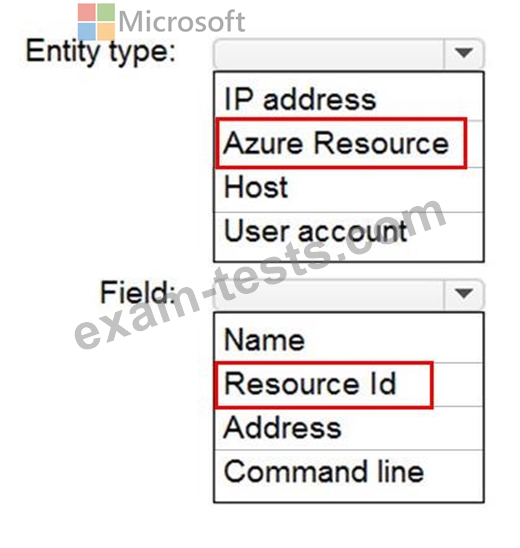
You need to hide Azure Defender alerts for the storage account.
Which entity type and field should you use in a suppression rule? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
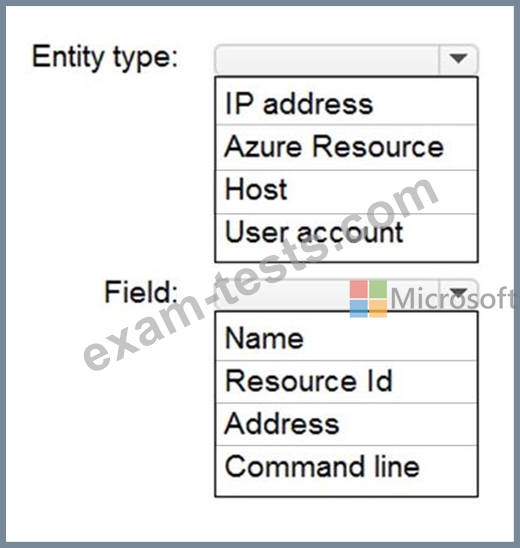
You need to hide Azure Defender alerts for the storage account.
Which entity type and field should you use in a suppression rule? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

Question 84
You have an Azure subscription that contains an Microsoft Sentinel workspace.
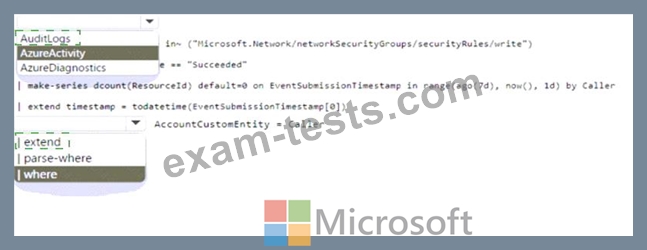
You need to create a hunting query using Kusto Query Language (KQL) that meets the following requirements:
* Identifies an anomalous number of changes to the rules of a network security group (NSG) made by the same security principal
* Automatically associates the security principal with an Microsoft Sentinel entity How should you complete the query? To answer, select the appropriate options in the answer area. NOTE:
Each correct selection is worth one point.
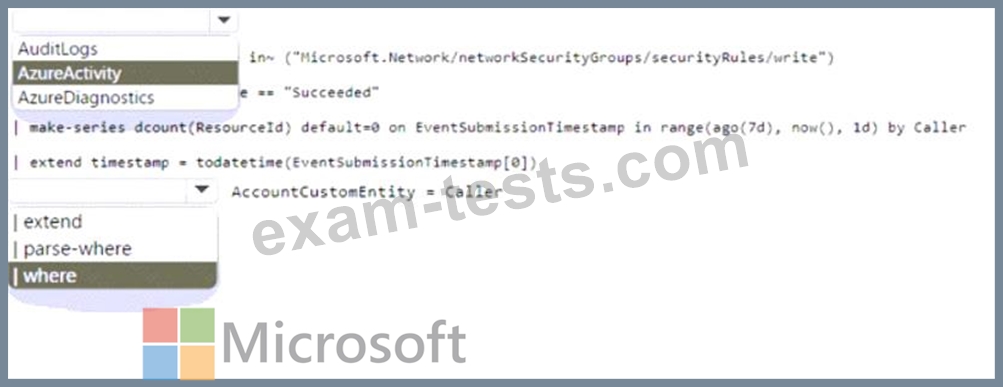
You need to create a hunting query using Kusto Query Language (KQL) that meets the following requirements:
* Identifies an anomalous number of changes to the rules of a network security group (NSG) made by the same security principal
* Automatically associates the security principal with an Microsoft Sentinel entity How should you complete the query? To answer, select the appropriate options in the answer area. NOTE:
Each correct selection is worth one point.

Question 85
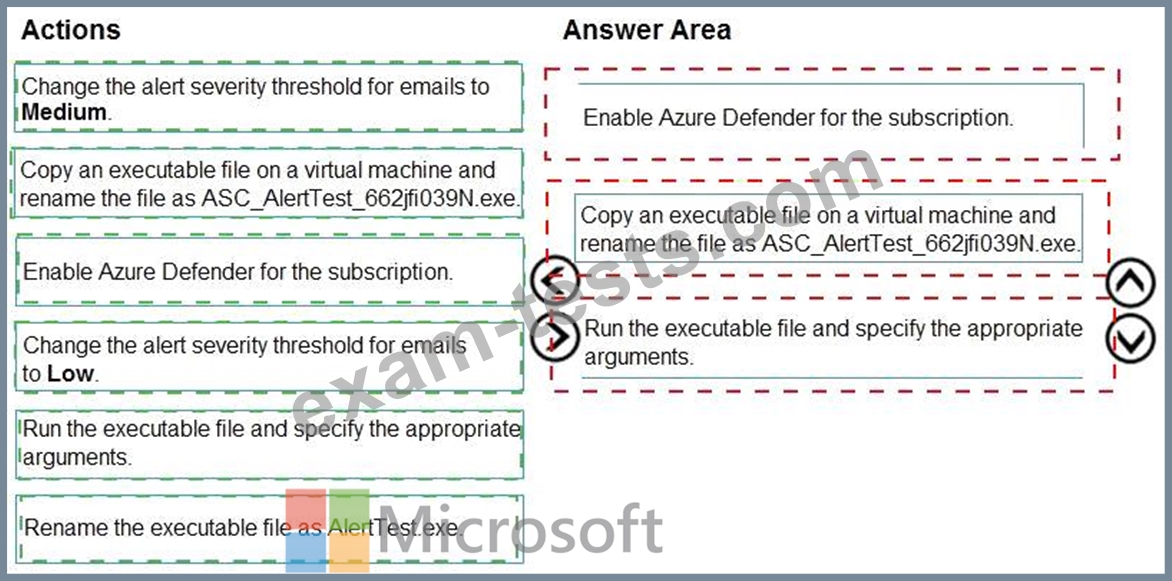
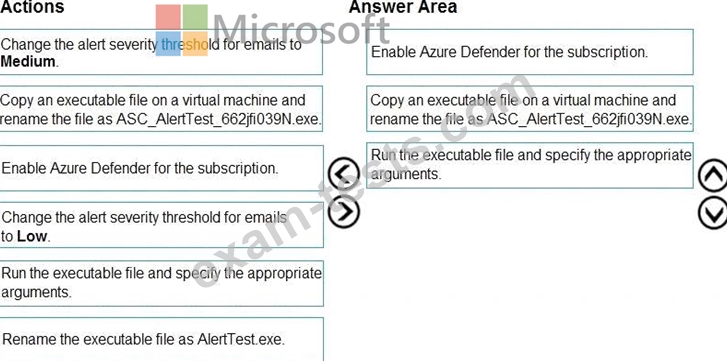
You create a new Azure subscription and start collecting logs for Azure Monitor.
You need to configure Azure Security Center to detect possible threats related to sign-ins from suspicious IP addresses to Azure virtual machines. The solution must validate the configuration.
Which three actions should you perform in a sequence? To answer, move the appropriate actions from the list of action to the answer area and arrange them in the correct order.
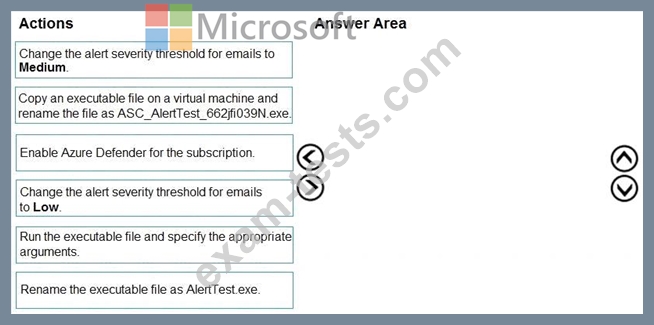
You need to configure Azure Security Center to detect possible threats related to sign-ins from suspicious IP addresses to Azure virtual machines. The solution must validate the configuration.
Which three actions should you perform in a sequence? To answer, move the appropriate actions from the list of action to the answer area and arrange them in the correct order.