Question 171
You are investigating a potential attack that deploys a new ransomware strain.
You plan to perform automated actions on a group of highly valuable machines that contain sensitive information.
You have three custom device groups.
You need to be able to temporarily group the machines to perform actions on the devices.
Which three actions should you perform? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
You plan to perform automated actions on a group of highly valuable machines that contain sensitive information.
You have three custom device groups.
You need to be able to temporarily group the machines to perform actions on the devices.
Which three actions should you perform? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
Question 172
You have a Microsoft 365 subscription
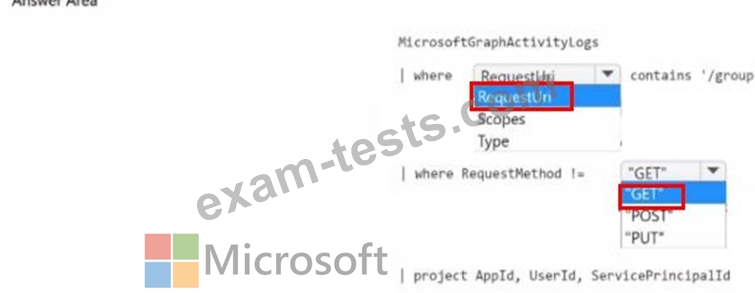
You need to identify all the security principals that submitted requests to change or delete groups. How should you complete the KQL query? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

You need to identify all the security principals that submitted requests to change or delete groups. How should you complete the KQL query? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

Question 173
You are investigating an incident by using Microsoft 365 Defender.
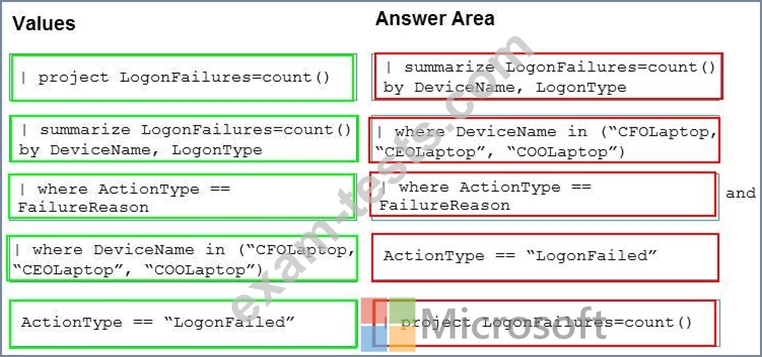
You need to create an advanced hunting query to detect failed sign-in authentications on three devices named CFOLaptop, CEOLaptop, and COOLaptop.
How should you complete the query? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
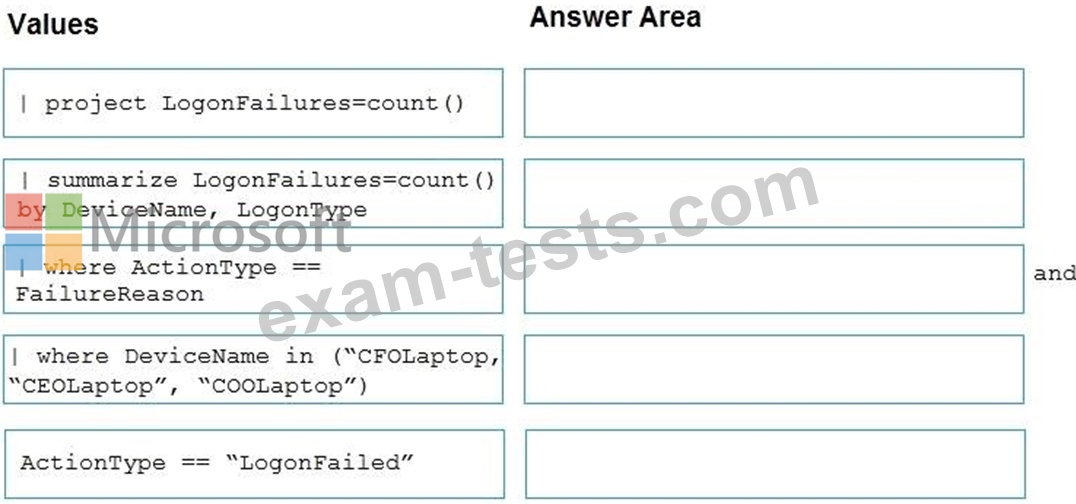
You need to create an advanced hunting query to detect failed sign-in authentications on three devices named CFOLaptop, CEOLaptop, and COOLaptop.
How should you complete the query? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

Question 174
You have an Azure subscription that contains an Microsoft Sentinel workspace.
You need to create a hunting query using Kusto Query Language (KQL) that meets the following requirements:
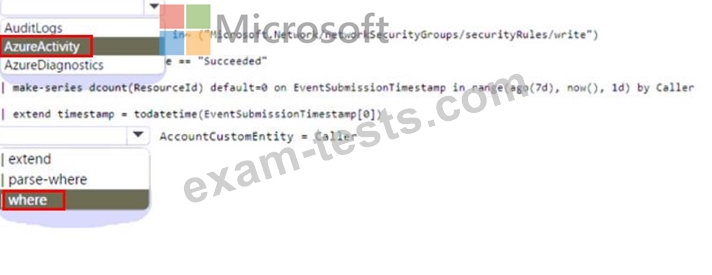
* Identifies an anomalous number of changes to the rules of a network security group (NSG) made by the same security principal
* Automatically associates the security principal with an Microsoft Sentinel entity How should you complete the query? To answer, select the appropriate options in the answer are a. NOTE: Each correct selection is worth one point.
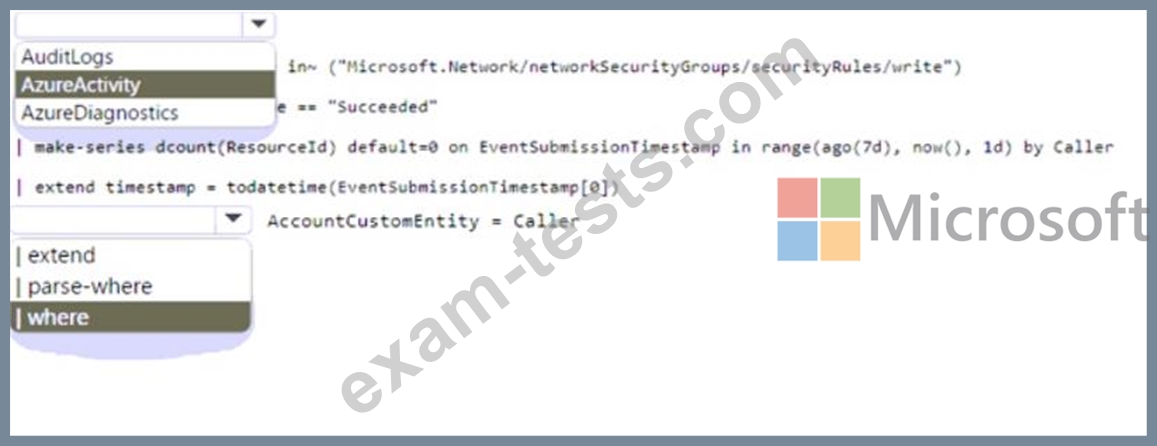
You need to create a hunting query using Kusto Query Language (KQL) that meets the following requirements:
* Identifies an anomalous number of changes to the rules of a network security group (NSG) made by the same security principal
* Automatically associates the security principal with an Microsoft Sentinel entity How should you complete the query? To answer, select the appropriate options in the answer are a. NOTE: Each correct selection is worth one point.

Question 175
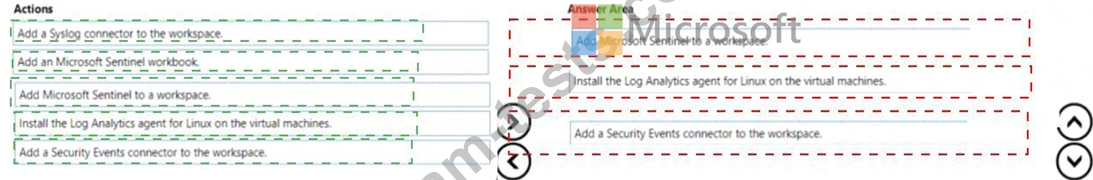
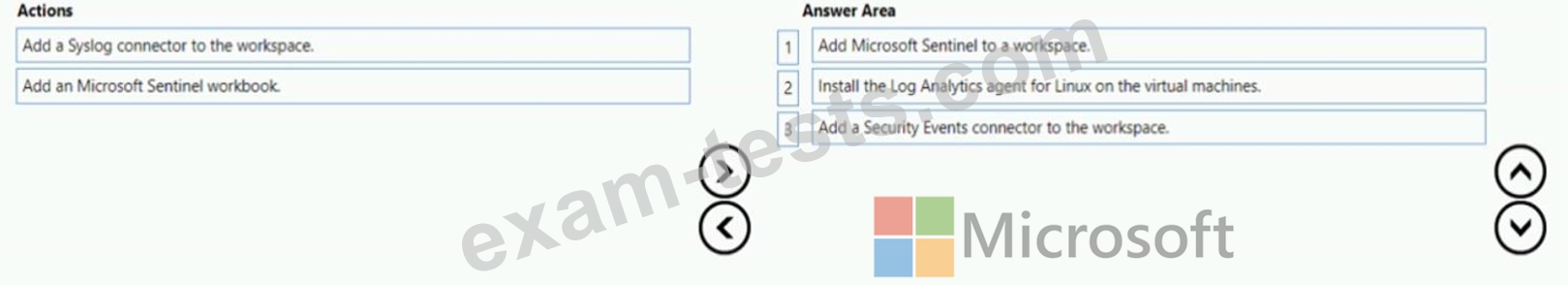
You have an Azure subscription that contains 100 Linux virtual machines.
You need to configure Microsoft Sentinel to collect event logs from the virtual machines.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.

You need to configure Microsoft Sentinel to collect event logs from the virtual machines.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.