Question 61
You have an Azure Active Directory (Azure AD) tenant that contains the users shown in the following table.
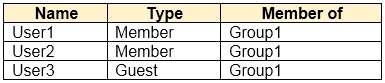
User1 is the owner of Group1.
You create an access review that has the following settings:
* Users to review: Members of a group
* Scope: Everyone
* Group: Group1
* Reviewers: Members (self)
Which users can perform access reviews for User3?

User1 is the owner of Group1.
You create an access review that has the following settings:
* Users to review: Members of a group
* Scope: Everyone
* Group: Group1
* Reviewers: Members (self)
Which users can perform access reviews for User3?
Question 62
You have a Microsoft 365 tenant.
The Azure Active Directory (Azure AD) tenant syncs to an on-premises Active Directory domain.
You plan to create an emergency-access administrative account named Emergency1. Emergency1 will be assigned the Global administrator role in Azure AD. Emergency1 will be used in the event of Azure AD functionality failures and on-premises infrastructure failures.
You need to reduce the likelihood that Emergency1 will be prevented from signing in during an emergency.
What should you do?
The Azure Active Directory (Azure AD) tenant syncs to an on-premises Active Directory domain.
You plan to create an emergency-access administrative account named Emergency1. Emergency1 will be assigned the Global administrator role in Azure AD. Emergency1 will be used in the event of Azure AD functionality failures and on-premises infrastructure failures.
You need to reduce the likelihood that Emergency1 will be prevented from signing in during an emergency.
What should you do?
Question 63
You have a Microsoft 365 tenant.
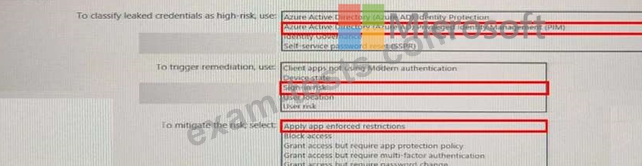
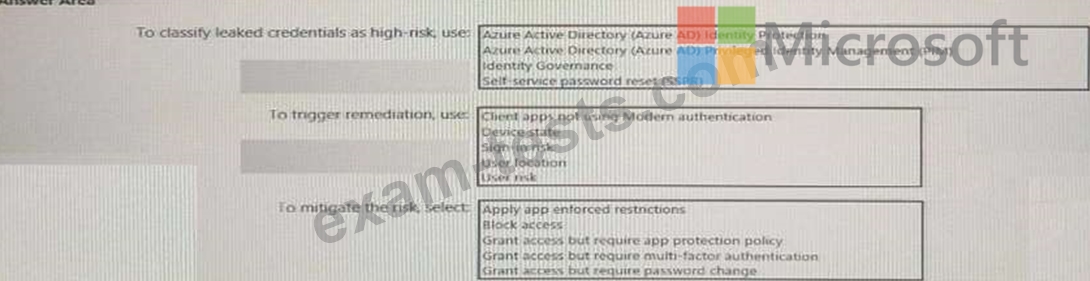
You need to identify users who have leaked credentials. The solution must meet the following requirements.
* Identity sign-Ins by users who ate suspected of having leaked credentials.
* Rag the sign-ins as a high risk event.
* Immediately enforce a control to mitigate the risk, while still allowing the user to access applications.
What should you use? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You need to identify users who have leaked credentials. The solution must meet the following requirements.
* Identity sign-Ins by users who ate suspected of having leaked credentials.
* Rag the sign-ins as a high risk event.
* Immediately enforce a control to mitigate the risk, while still allowing the user to access applications.
What should you use? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

Question 64
Your company has an Azure Active Directory (Azure AD) tenant named Contoso.com. The company has a business partner named Fabrikam, Inc.
Fabrikam uses Azure AD and has two verified domain names of fabrikam.com and litwarein.com Both domain names are sued for Fabrikam email addresses.
You create a connected organization for Fabrikam.
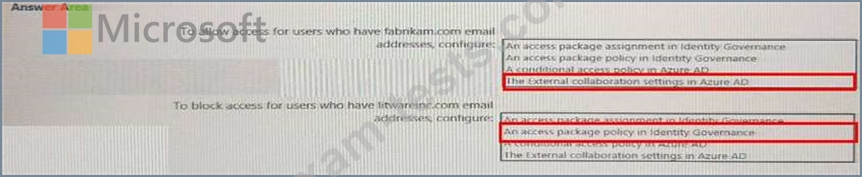
You need to ensure that the package1 will be accessible only to users who have fabrikam.com email addresses.
What should you do? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

Fabrikam uses Azure AD and has two verified domain names of fabrikam.com and litwarein.com Both domain names are sued for Fabrikam email addresses.
You create a connected organization for Fabrikam.
You need to ensure that the package1 will be accessible only to users who have fabrikam.com email addresses.
What should you do? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

Question 65
Your company has an Azure Active Directory (Azure AD) tenant named contosri.com. The company has the business partners shown in the following table.
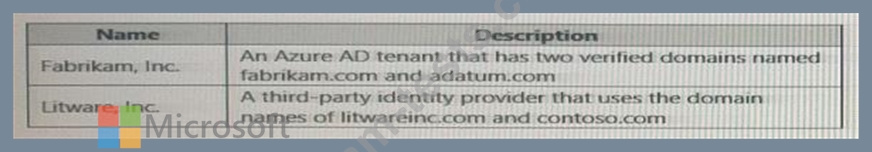
users can request access by using package 1.
Users at Fabrikam and Litware use ail then respective domain names for email addresses.
You plan to create an access package named packaqel that will be accessible only to the Fabrikam and Litware users.
You need to configure connected organizations for Fabrikam and litware so that any of their users can request access by using package1.
What is the minimum of connected organization that you should create.

users can request access by using package 1.
Users at Fabrikam and Litware use ail then respective domain names for email addresses.
You plan to create an access package named packaqel that will be accessible only to the Fabrikam and Litware users.
You need to configure connected organizations for Fabrikam and litware so that any of their users can request access by using package1.
What is the minimum of connected organization that you should create.