Question 31
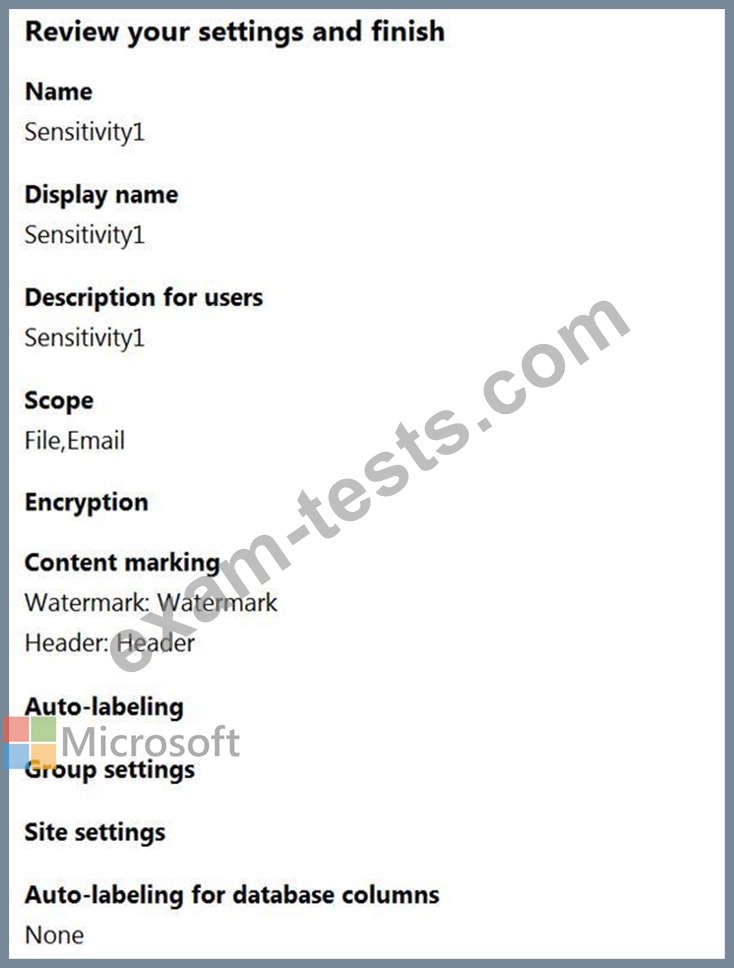
You create a sensitivity label as shown in the Sensitivity Label exhibit.
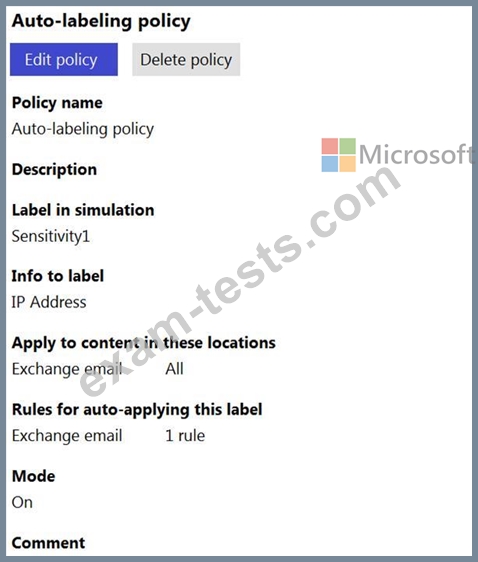
You create an auto-labeling policy as shown in the Auto Labeling Policy exhibit.
A user sends the following email:
From: [email protected]
To: [email protected]
Subject: Address List
Message Body:
Here are the lists that you requested.
Attachments:
<<File1.docx>>
<<File2.xml>>
Both attachments contain lists of IP addresses.
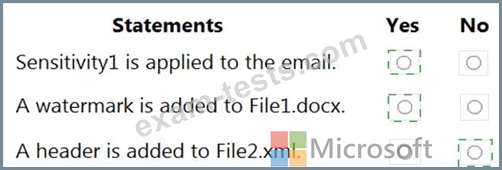
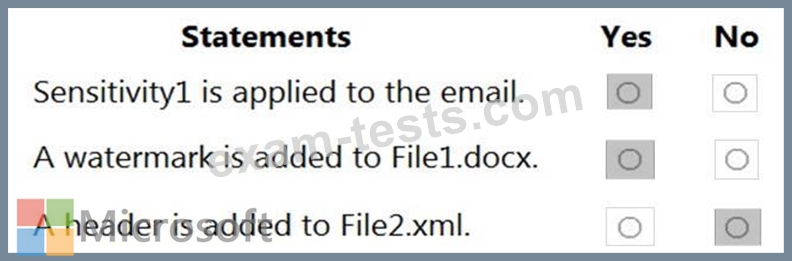
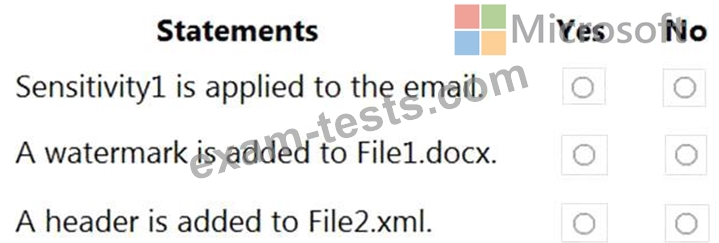
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

You create an auto-labeling policy as shown in the Auto Labeling Policy exhibit.

A user sends the following email:
From: [email protected]
To: [email protected]
Subject: Address List
Message Body:
Here are the lists that you requested.
Attachments:
<<File1.docx>>
<<File2.xml>>
Both attachments contain lists of IP addresses.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

Question 32
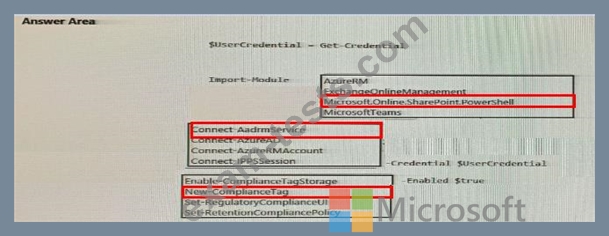
While creating a retention label, you discover that the following options are missing:
* Mark items as a record
* Mark items are a regular record
You need to ensure that the options are available when you create label in the Microsoft 365 compliance center.
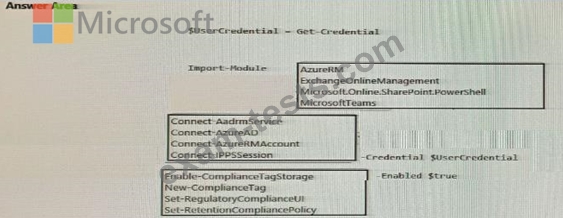
How should you complete the PowerShell script? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
* Mark items as a record
* Mark items are a regular record
You need to ensure that the options are available when you create label in the Microsoft 365 compliance center.
How should you complete the PowerShell script? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

Question 33
You need to meet the technical requirements for the confidential documents.
What should you created first, and what should you use for the detection method? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

What should you created first, and what should you use for the detection method? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

Question 34
You have a Microsoft 365 tenant that uses Microsoft Teams.
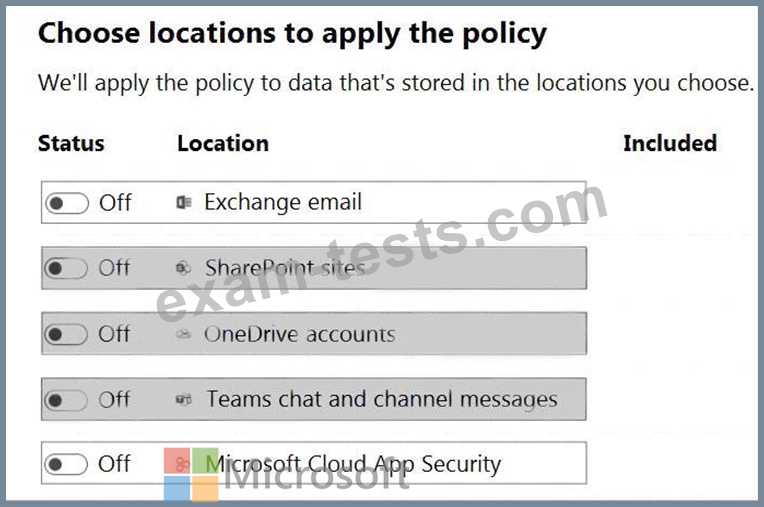
You create a data loss prevention (DLP) policy to prevent Microsoft Teams users from sharing sensitive information.
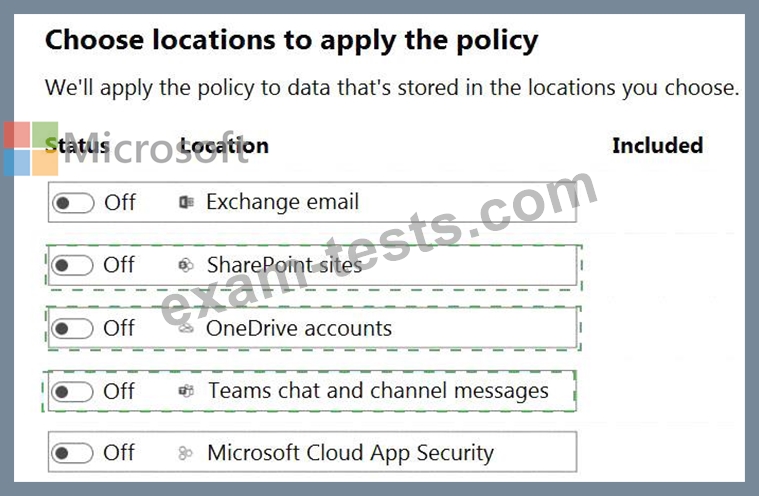
You need to identify which locations must be selected to meet the following requirements:
* Documents that contain sensitive information must not be shared inappropriately in Microsoft Teams.
* If a user attempts to share sensitive information during a Microsoft Teams chat session, the message must be deleted immediately.
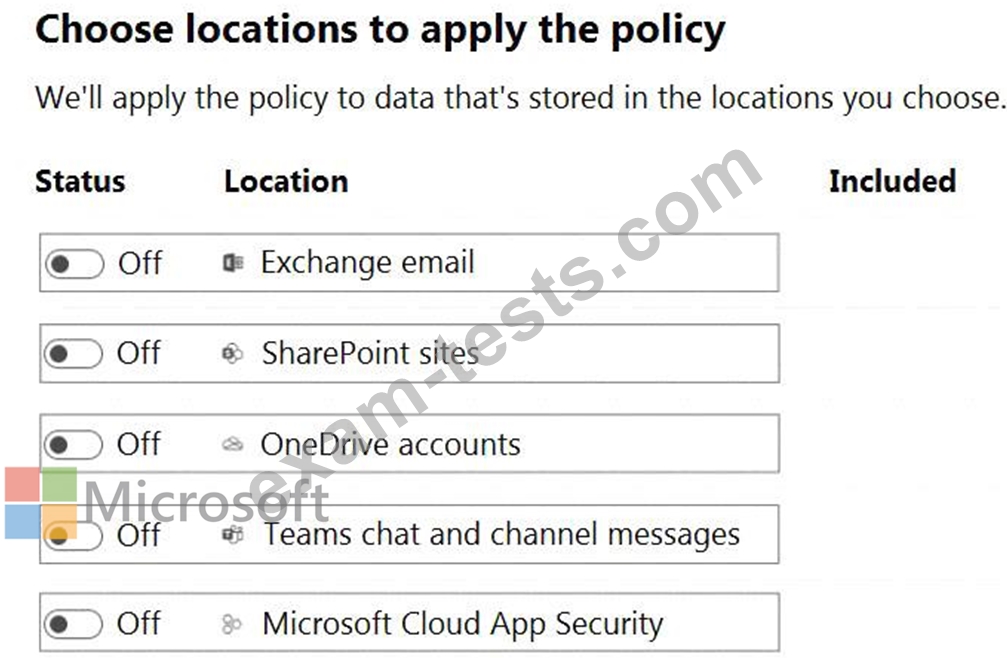
Which three locations should you select? To answer, select the appropriate locations in the answer area.
(Choose three.)
NOTE: Each correct selection is worth one point.
You create a data loss prevention (DLP) policy to prevent Microsoft Teams users from sharing sensitive information.
You need to identify which locations must be selected to meet the following requirements:
* Documents that contain sensitive information must not be shared inappropriately in Microsoft Teams.
* If a user attempts to share sensitive information during a Microsoft Teams chat session, the message must be deleted immediately.
Which three locations should you select? To answer, select the appropriate locations in the answer area.
(Choose three.)
NOTE: Each correct selection is worth one point.

Question 35
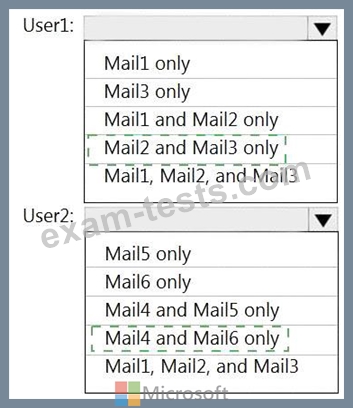
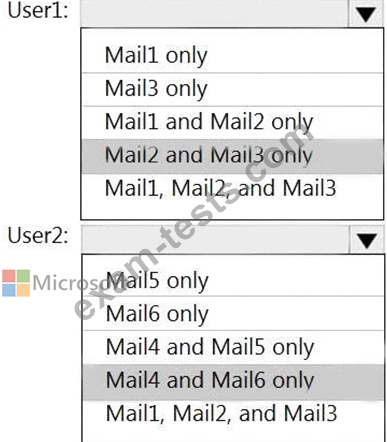
You have a Microsoft 365 tenant named contoso.com that contains two users named User1 and User2. The tenant uses Microsoft Office 365 Message Encryption (OME).
User1 plans to send emails that contain attachments as shown in the following table.
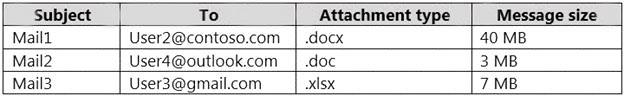
User2 plans to send emails that contain attachments as shown in the following table.
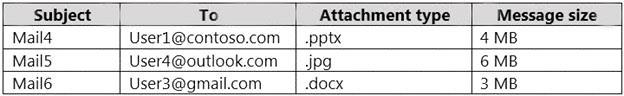
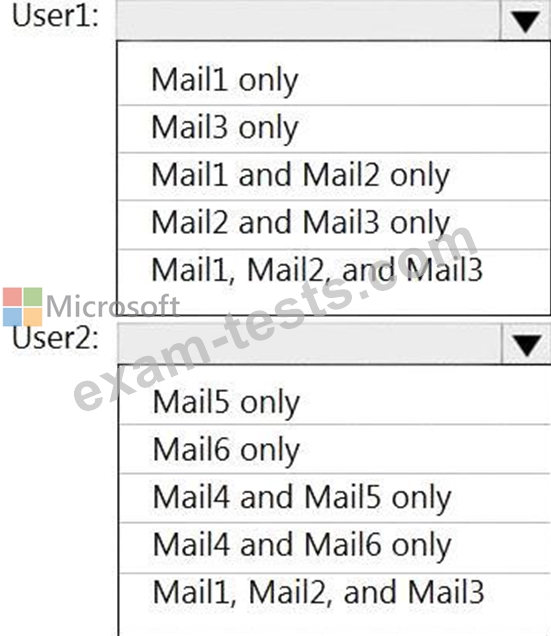
For which emails will the attachments be protected? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
User1 plans to send emails that contain attachments as shown in the following table.

User2 plans to send emails that contain attachments as shown in the following table.

For which emails will the attachments be protected? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.