Question 1
An attacker has successfully exfiltrated several non-salted password hashes from an online system. Given the logs below:
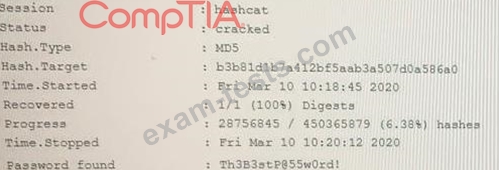
Which of the following BEST describes the type of password attack the attacker is performing?

Which of the following BEST describes the type of password attack the attacker is performing?
Question 2
An organization blocks user access to command-line interpreters but hackers still managed to invoke the interpreters using native administrative tools Which of the following should the security team do to prevent this from Happening in the future?
Question 3
A user reports constant lag and performance issues with the wireless network when working at a local coffee shop. A security analyst walks the user through an installation of Wireshark and get a five-minute pcap to analyze. The analyst observes the following output:

Which of the following attacks does the analyst MOST likely see in this packet capture?

Which of the following attacks does the analyst MOST likely see in this packet capture?
Question 4
A security auditor is reviewing vulnerability scan data provided by an internal security team. Which of the following BEST indicates that valid credentials were used?
Question 5
A company was recently breached Part of the company's new cybersecurity strategy is to centralize the logs from all security devices Which of the following components forwards the logs to a central source?

