Question 71
An organization has implemented a two-step verification process to protect user access to data that 6 stored in the could Each employee now uses an email address of mobile number a code to access the data. Which of the following authentication methods did the organization implement?
Question 72
Which of the following should be put in place when negotiating with a new vendor about the timeliness of the response to a significant outage or incident?
Question 73
A remote user recently took a two-week vacation abroad and brought along a corporate-owned laptop.
Upon returning to work, the user has been unable to connect the laptop to the VPN. Which of the following is the MOST likely reason for the user's inability to connect the laptop to the VPN?
Upon returning to work, the user has been unable to connect the laptop to the VPN. Which of the following is the MOST likely reason for the user's inability to connect the laptop to the VPN?
Question 74
Which of the following are requirements that must be configured for PCI DSS compliance? (Select TWO).
Question 75
An attacker has successfully exfiltrated several non-salted password hashes from an online system. Given the logs below:
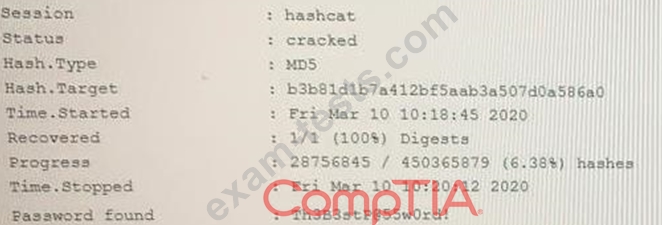
Which of the following BEST describes the type of password attack the attacker is performing?

Which of the following BEST describes the type of password attack the attacker is performing?

