Question 311
A security analyst is reviewing the output of a web server log and notices a particular account is attempting to transfer large amounts of money:
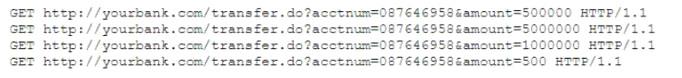
Which of the following types of attack is MOST likely being conducted?

Which of the following types of attack is MOST likely being conducted?
Question 312
A nationwide company is experiencing unauthorized logins at all hours of the day. The logins appear to originate from countries in which the company has no employees. Which of the following controls.
should the company consider using as part of its IAM strategy? (Select TWO).
should the company consider using as part of its IAM strategy? (Select TWO).
Question 313
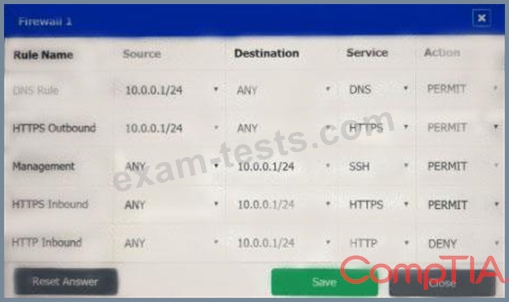
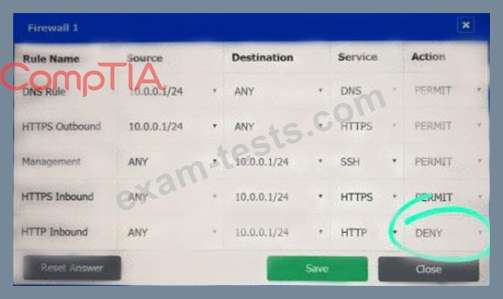
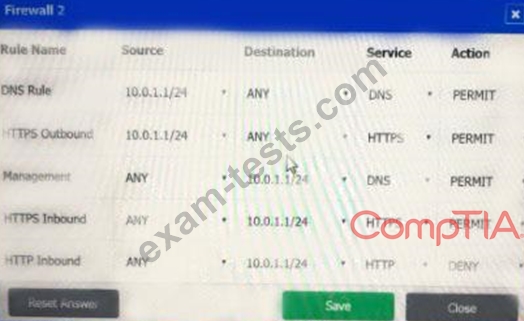
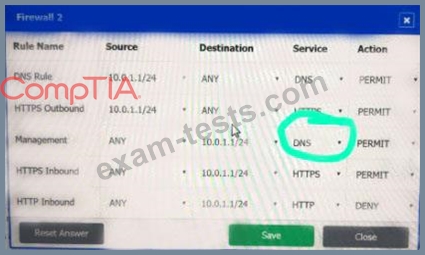
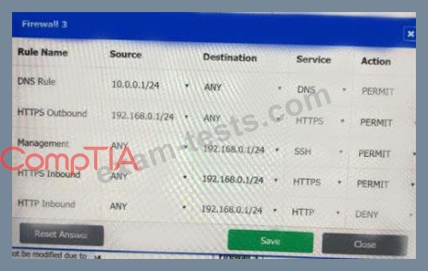
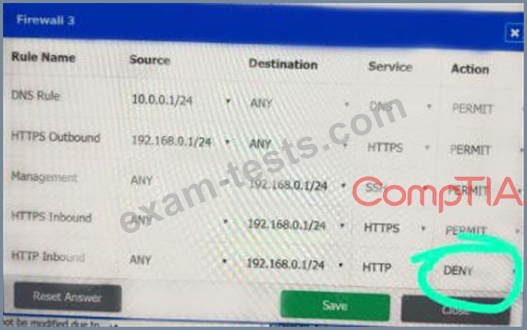
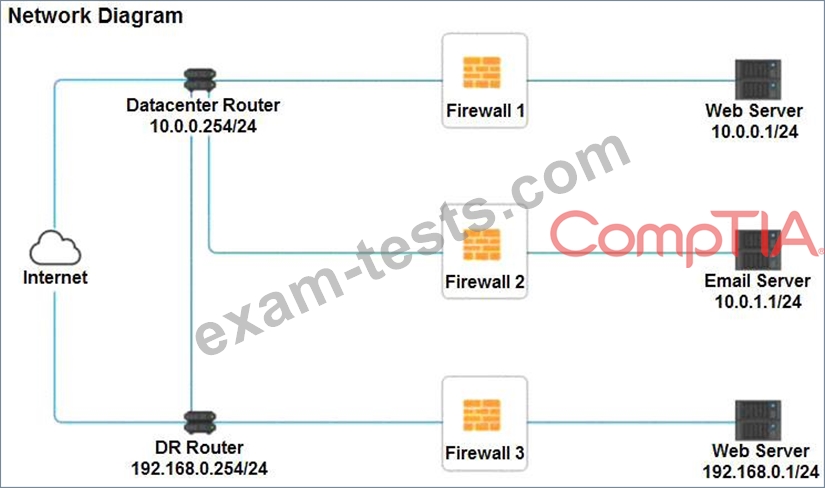
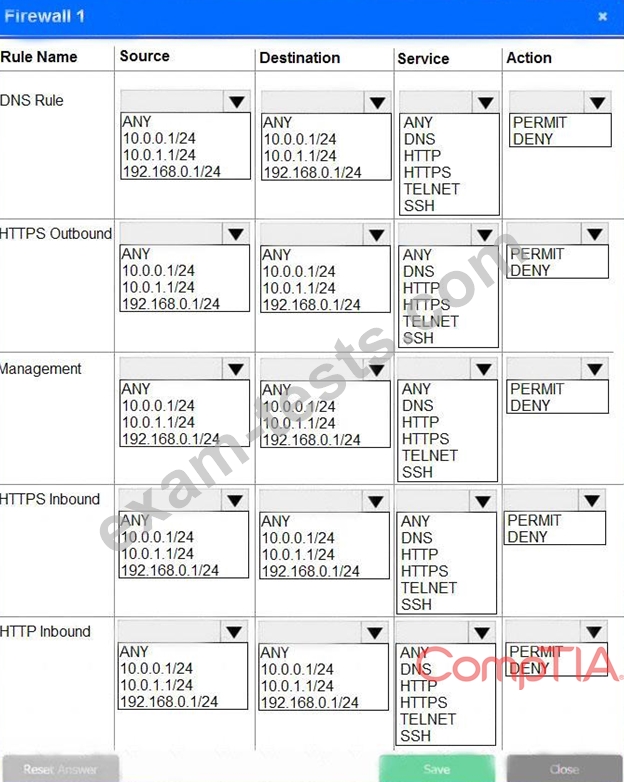
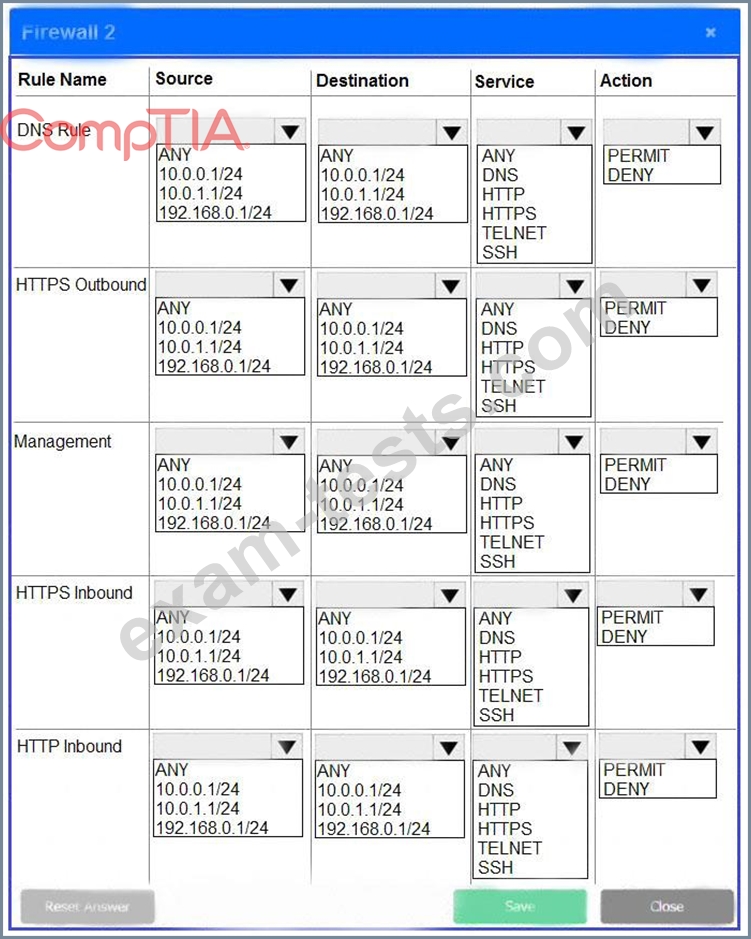
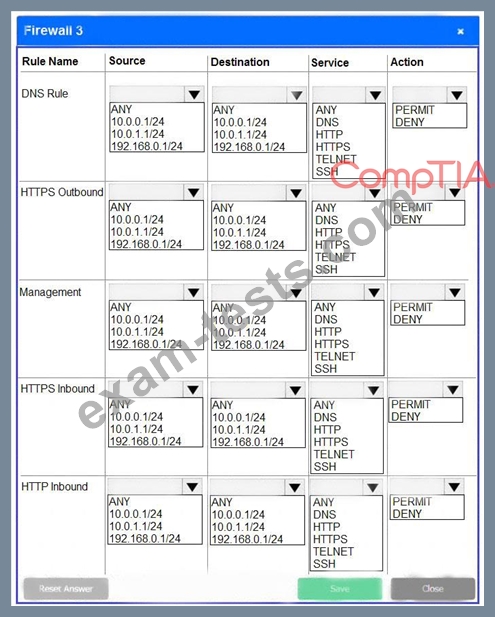
A company recently added a DR site and is redesigning the network. Users at the DR site are having issues browsing websites.
INSTRUCTIONS
Click on each firewall to do the following:
* Deny cleartext web traffic.
* Ensure secure management protocols are used.
* Resolve issues at the DR site.
The ruleset order cannot be modified due to outside constraints.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
INSTRUCTIONS
Click on each firewall to do the following:
* Deny cleartext web traffic.
* Ensure secure management protocols are used.
* Resolve issues at the DR site.
The ruleset order cannot be modified due to outside constraints.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.




Question 314
A company is required to continue using legacy software to support a critical service. Which of the following BEST explains a risk of this practice?
Question 315
The security team received a report of copyright infringement from the IP space of lire corporate network. The report provided a precise time stamp for the incident as well as the name of the copyrighted le. The analyst has been tasked with determining the infringing source machine and instructed to implement measures to prevent such incidents from occurring again. Which of the following is MOST capable of accomplishing both tasks?
Premium Bundle
Newest SY0-601 Exam PDF Dumps shared by BraindumpsPass.com for Helping Passing SY0-601 Exam! BraindumpsPass.com now offer the updated SY0-601 exam dumps, the BraindumpsPass.com SY0-601 exam questions have been updated and answers have been corrected get the latest BraindumpsPass.com SY0-601 pdf dumps with Exam Engine here: