Question 161
The SIEM at an organization has detected suspicious traffic coming a workstation in its internal network. An analyst in the SOC the workstation and discovers malware that is associated with a botnet is installed on the device A review of the logs on the workstation reveals that the privileges of the local account were escalated to a local administrator. To which of the following groups should the analyst report this real-world event?
Question 162
An organization wants to implement a biometric system with the highest likelihood that an unauthorized user will be denied access. Which of the following should the organization use to compare biometric solutions?
Question 163
A security administrator is analyzing the corporate wireless network The network only has two access points running on channels 1 and 11. While using airodump-ng. the administrator notices other access points are running with the same corporate ESSID on all available channels and with the same BSSID of one of the legitimate access ports Which of the following attacks in happening on the corporate network?
Question 164
A security analyst is reviewing the following attack log output:
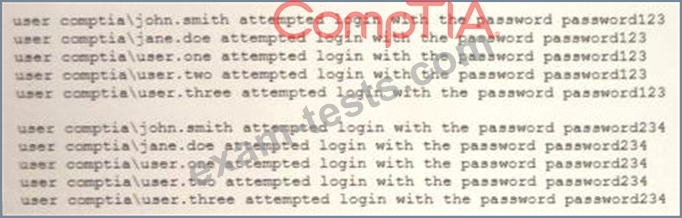
Which of the following types of attacks does this MOST likely represent?

Which of the following types of attacks does this MOST likely represent?
Question 165
A security analyst is reviewing the following output from a system:

Which of the following is MOST likely being observed?

Which of the following is MOST likely being observed?

