Question 171
An organization's help desk is flooded with phone calls from users stating they can no longer access certain websites. The help desk escalates the issue to the security team, as these websites were accessible the previous day. The security analysts run the following command: ipconfig /flushdns, but the issue persists. finally, an analyst changes the DNS server for an impacted machine, and the issue goes away. Which of the following attacks MOST likely occurred on the original DNS server?
Question 172
During an asset inventory, several assets, supplies, and miscellaneous items were noted as missing. The security manager has been asked to find an automated solution to detect any future theft of equipment. Which of the following would be BEST to implement?
Question 173
A security analyst is investigating an incident to determine what an attacker was able to do on a compromised laptop. The analyst reviews the following SIEM log:
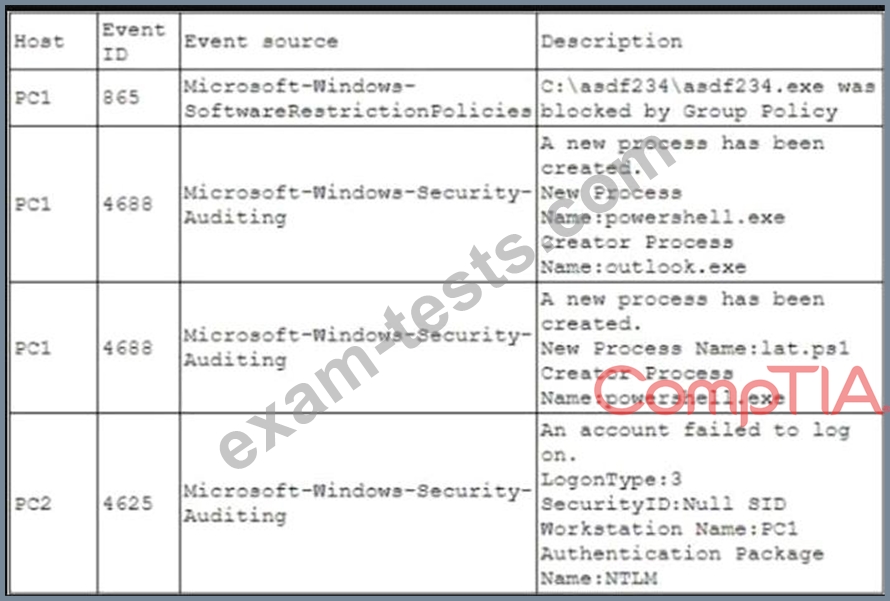
Which of the following describes the method that was used to compromise the laptop?

Which of the following describes the method that was used to compromise the laptop?
Question 174
In the middle of a cybersecurity, a security engineer removes the infected devices from the network and lock down all compromised accounts. In which of the following incident response phases is the security engineer currently operating?
Question 175
Which of the following BEST explains the difference between a data owner and a data custodian?

