Question 11
A security analyst is Investigating a malware incident at a company. The malware Is accessing a command-and-control website at www.comptia.com. All outbound Internet traffic is logged to a syslog server and stored in /logfiles/messages.
Which of the following commands would be BEST for the analyst to use on the syslog server to search for recent traffic to the command-and-control website?

Which of the following commands would be BEST for the analyst to use on the syslog server to search for recent traffic to the command-and-control website?

Question 12
A commercial cyber-threat intelligence organization observes IoCs across a variety of unrelated customers. Prior to releasing specific threat intelligence to other paid subscribers, the organization is MOST likely obligated by contracts to:
Question 13
Which of the following is the BEST reason to maintain a functional and effective asset management policy that aids in ensuring the security of an organization?
Question 14
A workwide manufacturing company has been experiencing email account compromised. In one incident, a user logged in from the corporate office in France, but then seconds later, the same user account attempted a login from Brazil. Which of the following account policies would BEST prevent this type of attack?
Question 15
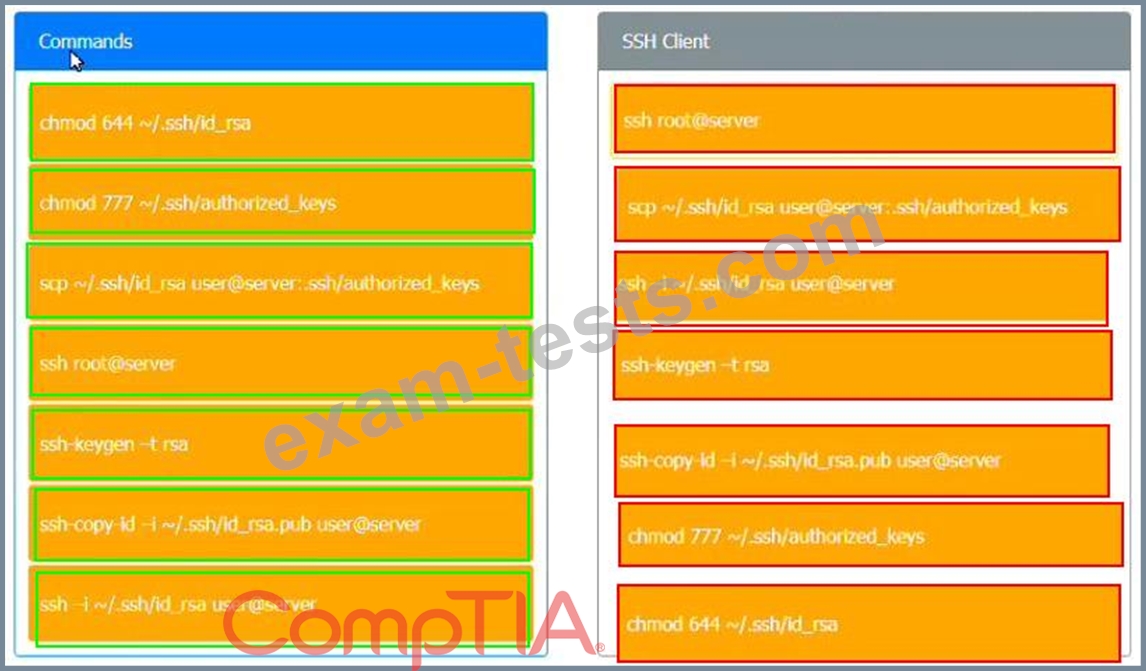
A security engineer is setting up passwordless authentication for the first time.
INSTRUCTIONS
Use the minimum set of commands to set this up and verify that it works. Commands cannot be reused.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.

INSTRUCTIONS
Use the minimum set of commands to set this up and verify that it works. Commands cannot be reused.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.