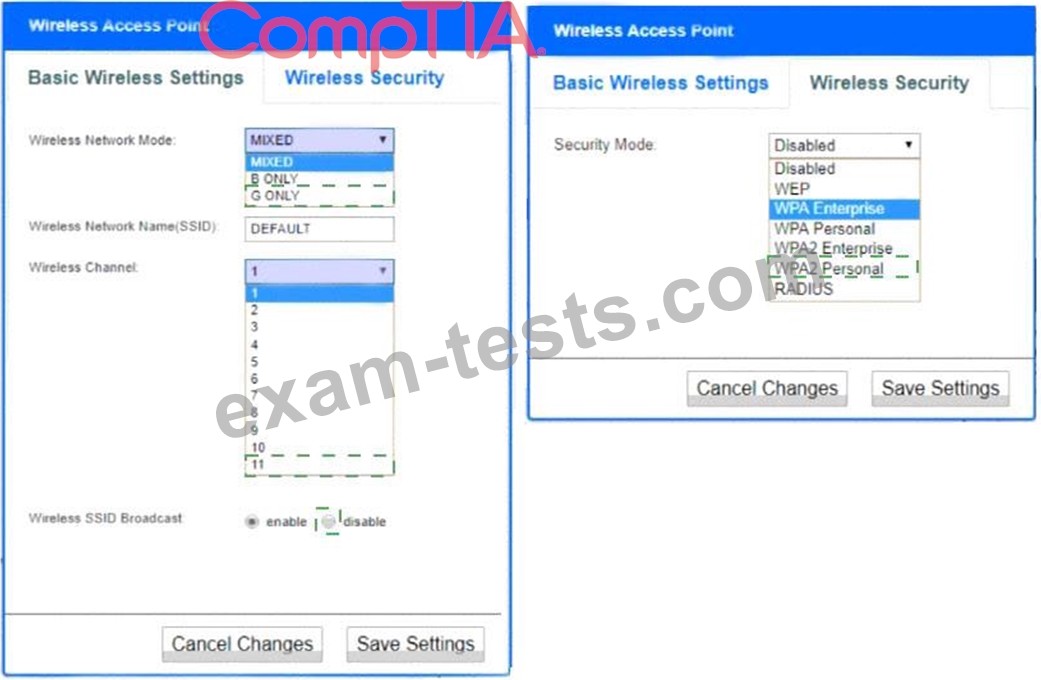
Question 286
While reviewing the wireless router, the systems administrator of a small business determines someone is spoofing the MAC address of an authorized device. Given the table below:
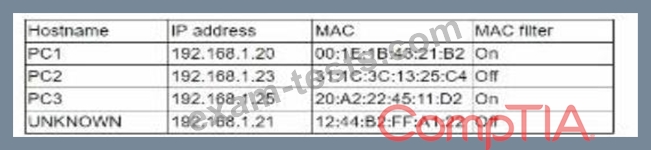
Which of the following should be the administrator's NEXT step to detect if there is a rogue system without impacting availability?

Which of the following should be the administrator's NEXT step to detect if there is a rogue system without impacting availability?
Question 287
A security analyst is concerned about critical vulnerabilities that have been detected on some applications running inside containers. Which of the following is the BEST remediation strategy?
Question 288
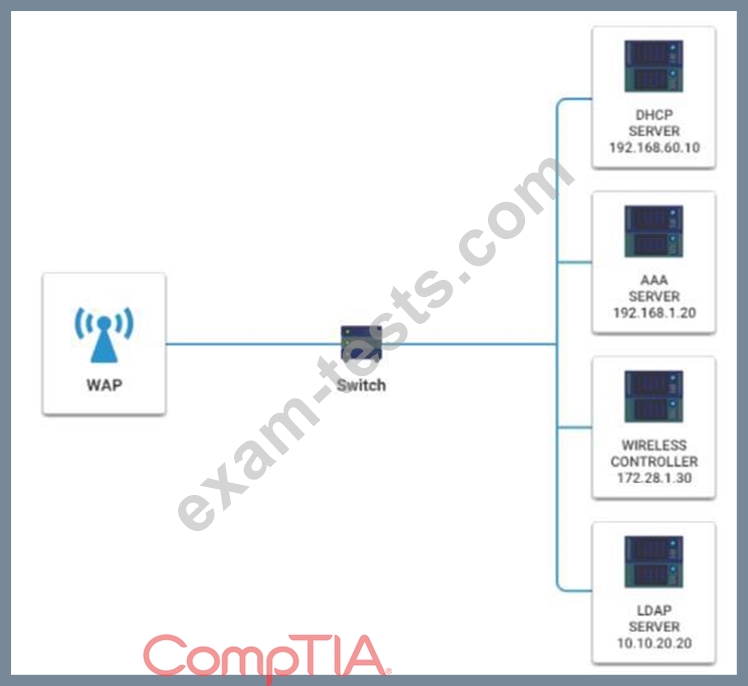
A newly purchased corporate WAP needs to be configured in the MOST secure manner possible.
INSTRUCTIONS
Please click on the below items on the network diagram and configure them accordingly:
* WAP
* DHCP Server
* AAA Server
* Wireless Controller
* LDAP Server
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
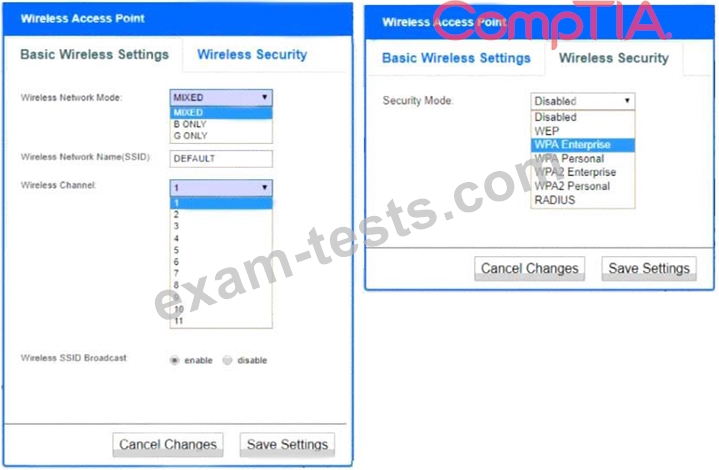
INSTRUCTIONS
Please click on the below items on the network diagram and configure them accordingly:
* WAP
* DHCP Server
* AAA Server
* Wireless Controller
* LDAP Server
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.


Question 289
A security manager runs Nessus scans of the network after every maintenance window. Which of the following is the security manger MOST likely trying to accomplish?
Question 290
Which of the following would cause a Chief Information Security Officer (CISO) the MOST concern regarding newly installed Internet-accessible 4K surveillance cameras?