Question 136
Which of the following should be monitored by threat intelligence researchers who search for leaked credentials?
Question 137
A customer has reported that an organization's website displayed an image of a smiley (ace rather than the expected web page for a short time two days earlier. A security analyst reviews log tries and sees the following around the lime of the incident:
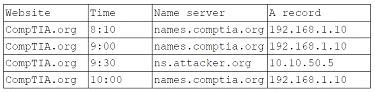
Which of the following is MOST likely occurring?

Which of the following is MOST likely occurring?
Question 138
During an investigation, a security manager receives notification from local authorities mat company proprietary data was found on a former employees home computer, The former employee's corporate workstation has since been repurposed, and the data on the hard drive has been overwritten Which of the following would BEST provide the security manager with enough details to determine when the data was removed from the company network?
Question 139
A user is concerned that a web application will not be able to handle unexpected or random input without crashing. Which of the following BEST describes the type of testing the user should perform?
Question 140
After a hardware incident, an unplanned emergency maintenance activity was conducted to rectify the issue.
Multiple alerts were generated on the SIEM during this period of time. Which of the following BEST explains what happened?
Multiple alerts were generated on the SIEM during this period of time. Which of the following BEST explains what happened?
Premium Bundle
Newest SY0-601 Exam PDF Dumps shared by BraindumpsPass.com for Helping Passing SY0-601 Exam! BraindumpsPass.com now offer the updated SY0-601 exam dumps, the BraindumpsPass.com SY0-601 exam questions have been updated and answers have been corrected get the latest BraindumpsPass.com SY0-601 pdf dumps with Exam Engine here:

