Question 131
A Linux systems administrator wants the ability to access systems remotely over SSH using RSA authentication. to which of the following files should the RSA token be added to allow this access?
Question 132
When logging in, an administrator must use a temporary six-digit code that is displayed on a key fob.
Which of the following has been implemented?
Which of the following has been implemented?
Question 133
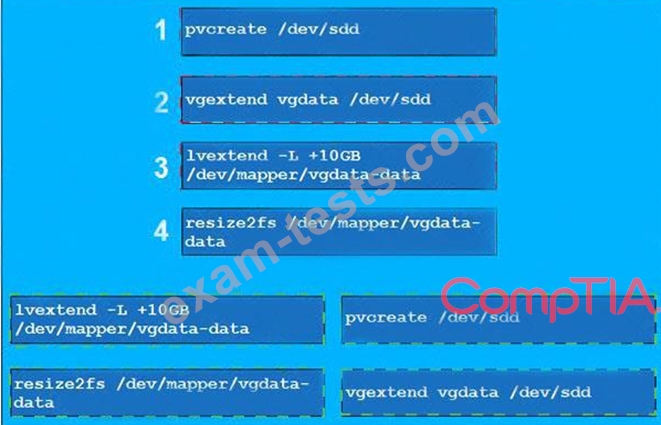
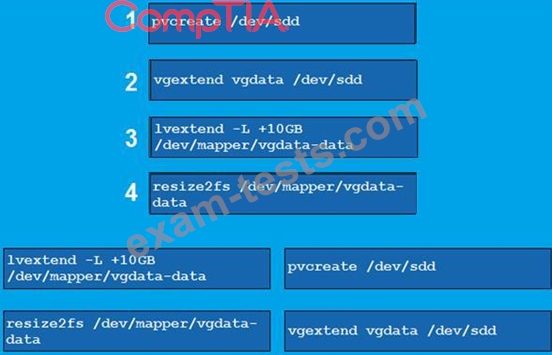
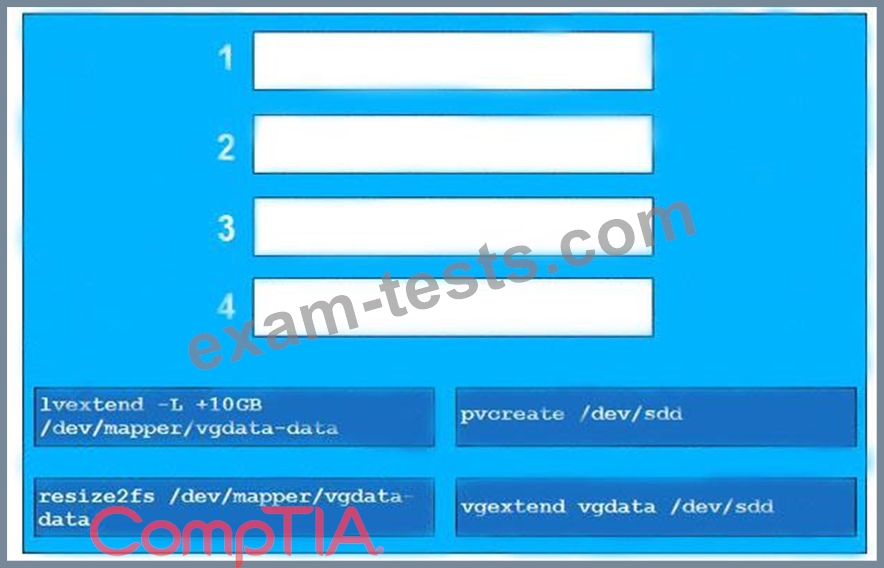
The lead Linux has added a disk, /dev/sdd, to a VM that is running out of disk space. Place the following steps in the correct order from first (1) to last (4) to add the disk to the existing LVM.

Question 134
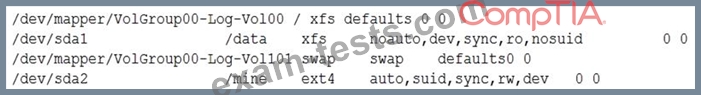
A junior systems administrator created a new filesystem /dev/sda1 with mountpoint /data and added it to the /etc/fstab for auto-mounting.
When the systems administrator tries to mount the file system, the system refuses. Given the output below:
Which of the following steps is necessary?
When the systems administrator tries to mount the file system, the system refuses. Given the output below:

Which of the following steps is necessary?
Question 135
A junior Linux administrator is installing patches using YUM. The administrator issues the following command:
yum list installed
The output of the command is as follows:
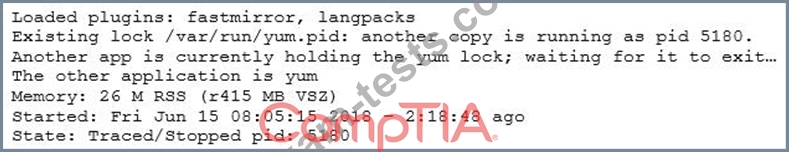
Given this scenario and the output, which of the following should the administrator do to address this issue?
yum list installed
The output of the command is as follows:

Given this scenario and the output, which of the following should the administrator do to address this issue?