Question 1
Which Check Point software blade provides visibility of users, groups and machines while also providing access control through identity-based policies?
Question 2
What are the three components for Check Point Capsule?
Question 3
A(n) _____ rule is created by an administrator and is located before the first and before last rules in the Rule Base.
Question 4
You want to reset SIC between smberlin and sgosaka.
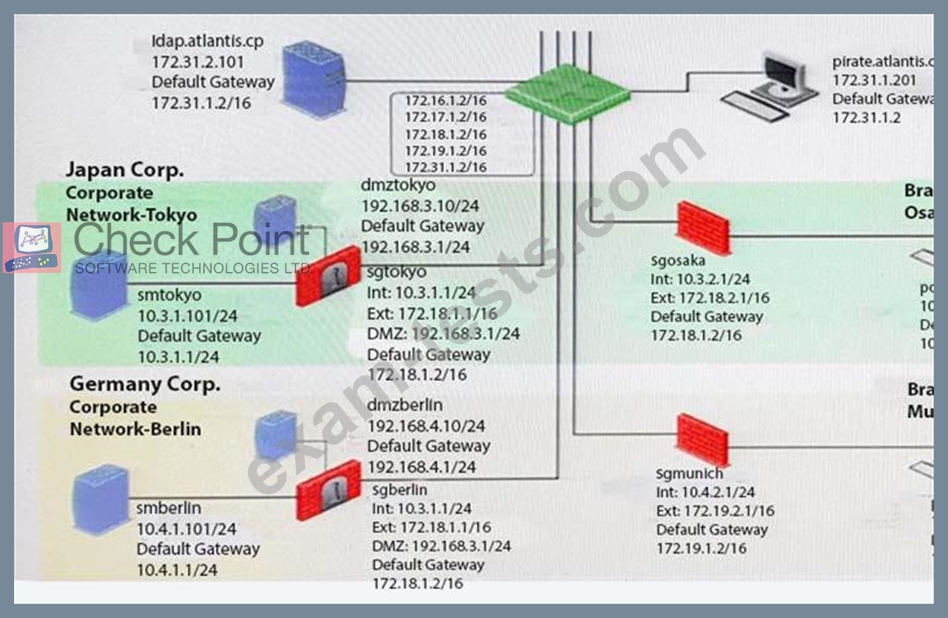
In SmartDashboard, you choose sgosaka, Communication, Reset. On sgosaka, you start cpconfig, choose Secure Internal Communication and enter the new SIC Activation Key. The screen reads The SIC was successfully initialized and jumps back to the menu. When trying to establish a connection, instead of a working connection, you receive this error message:
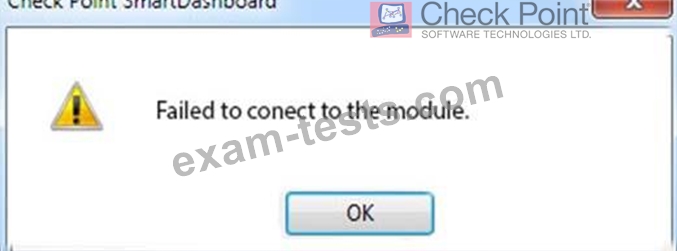
What is the reason for this behavior?

In SmartDashboard, you choose sgosaka, Communication, Reset. On sgosaka, you start cpconfig, choose Secure Internal Communication and enter the new SIC Activation Key. The screen reads The SIC was successfully initialized and jumps back to the menu. When trying to establish a connection, instead of a working connection, you receive this error message:

What is the reason for this behavior?
Question 5
In what way is Secure Network Distributor (SND) a relevant feature of the Security Gateway?

