Question 6
You are the administrator for Alpha Corp. You have logged into your R80 Management server. You are making some changes in the Rule Base and notice that rule No.6 has a pencil icon next to it.
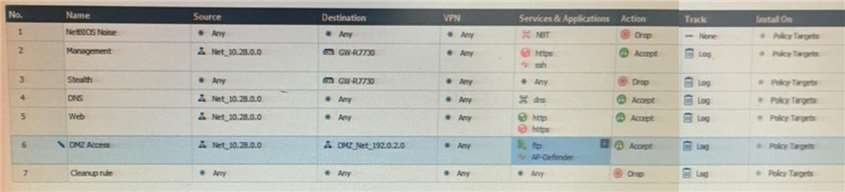
What does this mean?

What does this mean?
Question 7
Which Threat Prevention Software Blade provides protection from malicious software that can infect your network computers?
Question 8
What will be the effect of running the following command on the Security Management Server?
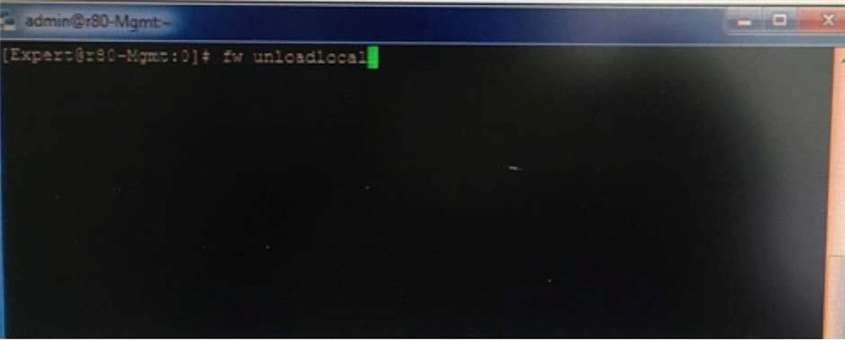

Question 9
What is the purpose of the Stealth Rule?
Question 10
Fill in the blank: When LDAP is integrated with Check Point Security Management, it is then referred to as
_______
_______

