Question 91
You work as a security administrator for a large company. CSO of your company has attended a security conference where he has learnt how hackers constantly modify their strategies and techniques to evade detection and reach corporate resources. He wants to make sure that his company has the right protections in place. Check Point has been selected for the security vendor. Which Check Point products protects BEST against malware and zero-day attacks while ensuring quick delivery of safe content to your users?
Question 92
Why would an administrator see the message below?
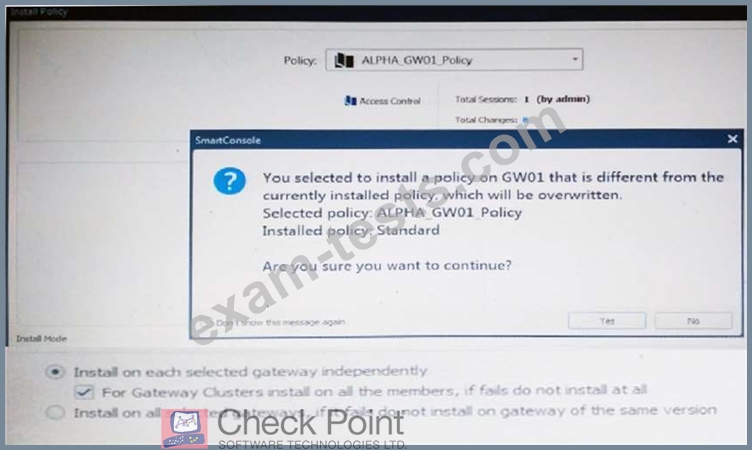

Question 93
Which one of the following is the preferred licensing model? Select the Best answer.
Question 94
Review the rules. Assume domain UDP is enabled in the implied rules.
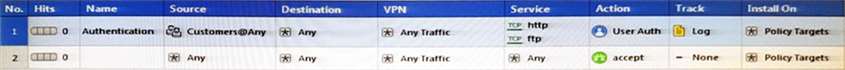
What happens when a user from the internal network tries to browse to the internet using
HTTP? The user:

What happens when a user from the internal network tries to browse to the internet using
HTTP? The user:
Question 95
Vanessa is expecting a very important Security Report. The Document should be sent as an attachment via e-mail. An e-mail with Security_report.pdf file was delivered to her e-mail inbox. When she opened the PDF file, she noticed that the file is basically empty and only few lines of text are in it. The report is missing some graphs, tables and links. Which component of SandBlast protection is her company using on a Gateway?


