Question 46
Provide very wide coverage for all products and protocols, with noticeable performance impact.
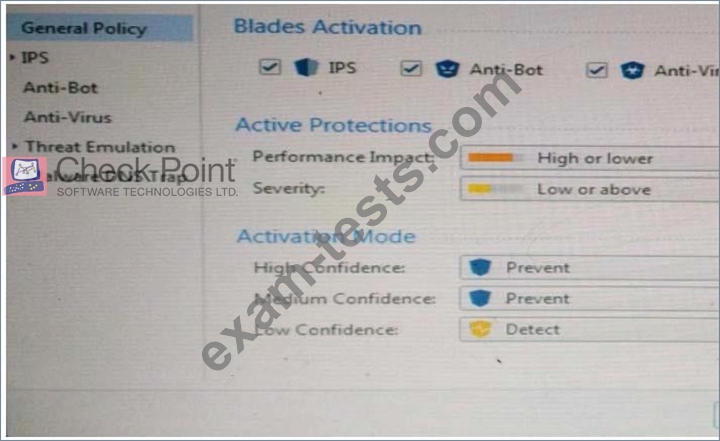
How could you tune the profile in order to lower the CPU load still maintaining security at good level?
Select the BEST answer.

How could you tune the profile in order to lower the CPU load still maintaining security at good level?
Select the BEST answer.
Question 47
Provide very wide coverage for all products and protocols, with noticeable performance impact.
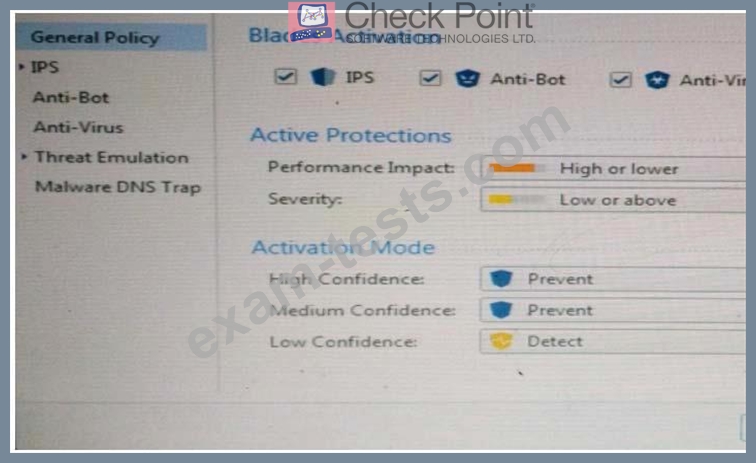
How could you tune the profile in order to lower the CPU load still maintaining security at good level?
Select the BEST answer.

How could you tune the profile in order to lower the CPU load still maintaining security at good level?
Select the BEST answer.
Question 48
There are two R77.30 Security Gateways in the Firewall Cluster. They are named FW_A and FW_B. The cluster is configured to work as HA (High availability) with default cluster configuration. FW_A is configured to have higher priority than FW_B. FW_A was active and processing the traffic in the morning. FW_B was standby. Around 1100 am, its interfaces went down and this caused a failover. FW_B became active. After an hour, FW_A's interface issues were resolved and it became operational. When it re-joins the cluster, will it become active automatically?
Question 49
Which policy type is used to enforce bandwidth and traffic control rules?
Question 50
Which of the following is a hash algorithm?

