Question 1
Which step does a Citrix Architect need to ensure during the Define phase when following the Citrix Methodology?
Question 2
Scenario: A Citrix Architect needs to design a hybrid XenApp and XenDesktop environment which will include Citrix Cloud as well as resource locations in an on-premises datacenter and Microsoft Azure.
Organizational details and requirements are as follows:
* Active XenApp and XenDesktop Service subscription
* No existing NetScaler deployment
* Global Server Load Balancing is used to direct connection requests to Location B, if the StoreFront server in Location B fails, connections should be directed to Location A.
Click the Exhibit button to view the conceptual environment architecture.
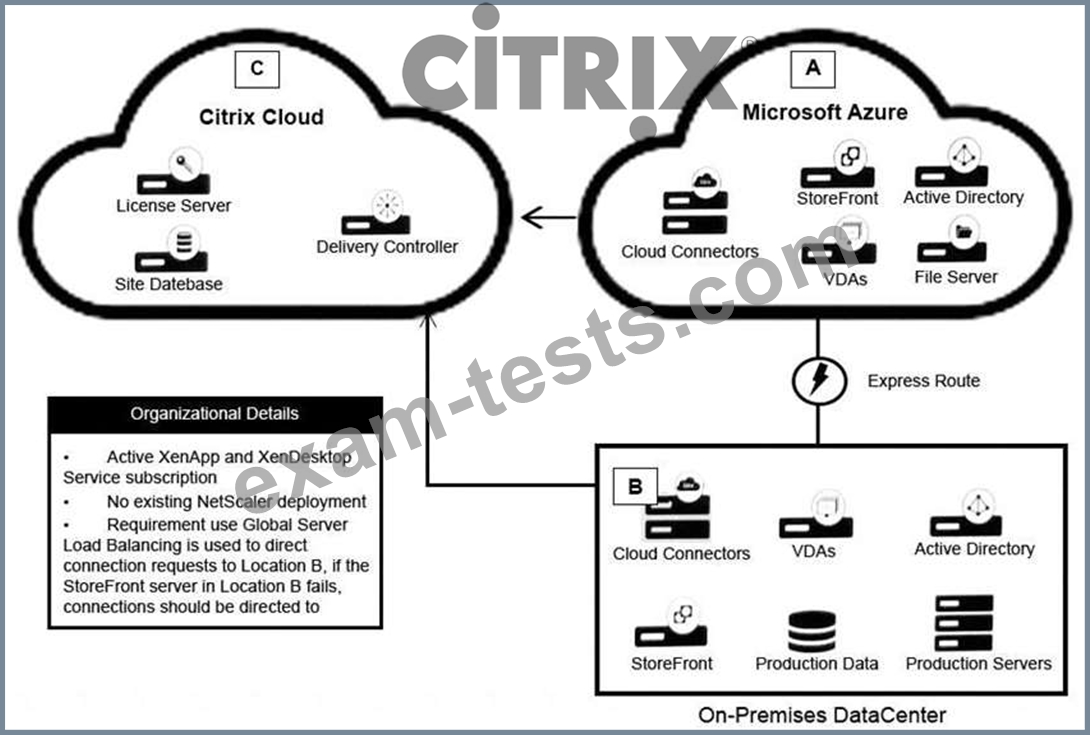
The architect should use _____ in Location A, and should use ________ in Location B.
(Choose the correct option to complete the sentence.)
Organizational details and requirements are as follows:
* Active XenApp and XenDesktop Service subscription
* No existing NetScaler deployment
* Global Server Load Balancing is used to direct connection requests to Location B, if the StoreFront server in Location B fails, connections should be directed to Location A.
Click the Exhibit button to view the conceptual environment architecture.

The architect should use _____ in Location A, and should use ________ in Location B.
(Choose the correct option to complete the sentence.)
Question 3
Scenario: A Citrix Architect has met with a team of Workspacelab members for a design discussion. They have captured the following requirements for the Citrix ADC design project:
* Multi-factor authentication must be configured the Citrix Gateway virtual server.
* The Citrix Gateway virtual server is integrated with the Citrix Virtual Apps and Desktops environment.
* Load balancing must be configured for the StoreFront server.
* Authentication must be deployed for the users from the workspacelab.com and vendorlab.com domains.
* The logon page must have the workspacelab logo on it.
* Certificate verification must be performed to identify and extract the username.
* The client certificate must have UserPrincipalName as a subject.
* All the managed workstations for the workspacelab users must have the client identification certificate installed on them.
* The workspacelab users connecting from the internal network should be authenticated using LDAP.
* The workspacelab users connecting from the external network should be authenticated using LDAP and RADIUS.
* The vendorlab users should be authenticated using Active Directory Federation Service.
* The user credentials must NOT be shared between workspacelab and vendorlab.
* Single Sign-on must be performed between StoreFront and Citrix Gateway.
* A domain drop down list must be provided if the user connects to the Citrix Gateway virtual server externally.
* The domain of the user connecting externally must be identified using the domain selected from the domain drop down list.
Which authentication policy must the architect execute first to meet the design requirements?
* Multi-factor authentication must be configured the Citrix Gateway virtual server.
* The Citrix Gateway virtual server is integrated with the Citrix Virtual Apps and Desktops environment.
* Load balancing must be configured for the StoreFront server.
* Authentication must be deployed for the users from the workspacelab.com and vendorlab.com domains.
* The logon page must have the workspacelab logo on it.
* Certificate verification must be performed to identify and extract the username.
* The client certificate must have UserPrincipalName as a subject.
* All the managed workstations for the workspacelab users must have the client identification certificate installed on them.
* The workspacelab users connecting from the internal network should be authenticated using LDAP.
* The workspacelab users connecting from the external network should be authenticated using LDAP and RADIUS.
* The vendorlab users should be authenticated using Active Directory Federation Service.
* The user credentials must NOT be shared between workspacelab and vendorlab.
* Single Sign-on must be performed between StoreFront and Citrix Gateway.
* A domain drop down list must be provided if the user connects to the Citrix Gateway virtual server externally.
* The domain of the user connecting externally must be identified using the domain selected from the domain drop down list.
Which authentication policy must the architect execute first to meet the design requirements?
Question 4
Scenario: A Citrix Architect has set up Citrix ADC MPX devices in high availability mode with version
12.0.53.13 nc. These are placed behind a Cisco ASA 5505 firewall. The Cisco ASA firewall is configured to block traffic using access control lists. The network address translation (NAT) is also performed on the firewall.
The following requirements were captured by the architect during the discussion held as part of the Citrix ADC security implementation project with the customers security team:
The Citrix ADC MPX device:
* should monitor the rate of traffic either on a specific virtual entity or on the device It should be able to mitigate the attacks from a hostile client sending a flood of requests. The Citrix ADC device should be able to stop the HTTP TCP. and DNS based requests
* needs to protect backend servers from overloading
* needs to queue all the incoming requests on the virtual server level instead of the service level
* should provide access to resources on the basis of priority
* should provide protection against well-known Windows exploits virus-infected personal computers, centrally managed automated botnets, compromised webservers, known spammers/hackers, and phishing proxies
* should provide flexibility to enforce the desired level of security check inspections for the requests originating from a specific geolocation database.
* should block the traffic based on a pre-determined header length. URL length and cookie length. The device should ensure that characters such as a single straight quote ('): backslash (\); and semicolon (;) are either blocked, transformed, or dropped while being sent to the backend server.
Which security feature should the architect configure to meet these requirements?
12.0.53.13 nc. These are placed behind a Cisco ASA 5505 firewall. The Cisco ASA firewall is configured to block traffic using access control lists. The network address translation (NAT) is also performed on the firewall.
The following requirements were captured by the architect during the discussion held as part of the Citrix ADC security implementation project with the customers security team:
The Citrix ADC MPX device:
* should monitor the rate of traffic either on a specific virtual entity or on the device It should be able to mitigate the attacks from a hostile client sending a flood of requests. The Citrix ADC device should be able to stop the HTTP TCP. and DNS based requests
* needs to protect backend servers from overloading
* needs to queue all the incoming requests on the virtual server level instead of the service level
* should provide access to resources on the basis of priority
* should provide protection against well-known Windows exploits virus-infected personal computers, centrally managed automated botnets, compromised webservers, known spammers/hackers, and phishing proxies
* should provide flexibility to enforce the desired level of security check inspections for the requests originating from a specific geolocation database.
* should block the traffic based on a pre-determined header length. URL length and cookie length. The device should ensure that characters such as a single straight quote ('): backslash (\); and semicolon (;) are either blocked, transformed, or dropped while being sent to the backend server.
Which security feature should the architect configure to meet these requirements?
Question 5
Scenario: A Citrix Architect and a team of Workspacelab members met to discuss a Citrix ADC design project. They captured the following requirements from this design discussion:
* All three (3) Workspacelab sites (DC, NDR, and DR) will have similar Citrix ADC configurations and design.
* The external Citrix ADC MPX appliances will have Global Server Load Balancing (GSLB) configured and deployed in Active/Active mode.
* ADNS service should be configured on the Citrix ADC to make it authoritative for domain nsg.workspaceIab.com.
* In GSLB deployment, the DNS resolution should be performed to connect the user to the site with least network latency.
* On the internal Citrix ADC, load balancing for StoreFront services, Citrix XML services, and Citrix Director services must be configured.
* On the external Citrix ADC, the Gateway virtual server must be configured in ICA proxy mode.
Which GSLB method should the architect utilize to meet the design requirements?
* All three (3) Workspacelab sites (DC, NDR, and DR) will have similar Citrix ADC configurations and design.
* The external Citrix ADC MPX appliances will have Global Server Load Balancing (GSLB) configured and deployed in Active/Active mode.
* ADNS service should be configured on the Citrix ADC to make it authoritative for domain nsg.workspaceIab.com.
* In GSLB deployment, the DNS resolution should be performed to connect the user to the site with least network latency.
* On the internal Citrix ADC, load balancing for StoreFront services, Citrix XML services, and Citrix Director services must be configured.
* On the external Citrix ADC, the Gateway virtual server must be configured in ICA proxy mode.
Which GSLB method should the architect utilize to meet the design requirements?

