Question 6
Which statement is applicable to Citrix Gateway split tunneling?
Question 7
Scenario: A Citrix Architect needs to design a new NetScaler Gateway deployment to provide secure RDP access to backend Windows machines.
Click the Exhibit button to view additional requirements collected by the architect during the design discussions.
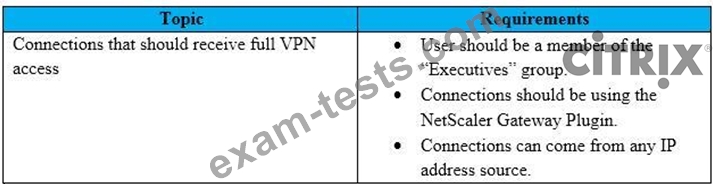
To meet the customer requirements, the architect should deploy the RDP proxy through _______, using a
_________ solution. (Choose the correct option to complete the sentence.)
Click the Exhibit button to view additional requirements collected by the architect during the design discussions.

To meet the customer requirements, the architect should deploy the RDP proxy through _______, using a
_________ solution. (Choose the correct option to complete the sentence.)
Question 8
Scenario: A Citrix Architect has deployed an authentication setup for the load balancing virtual server for the SAP application. The authentication is being performed using RADIUS and LDAP. RADIUS is the first factor, and LDAP is the second factor in the authentication. The Single Sign-on with SAP application should be performed using LDAP credentials. Which session profile should be used to perform the Single Sign-on?
Question 9
Which request can a Citrix Architect utilize to create a NITRO API command to add a NetScaler appliance with NSIP address 10.102.29.60 to the cluster?
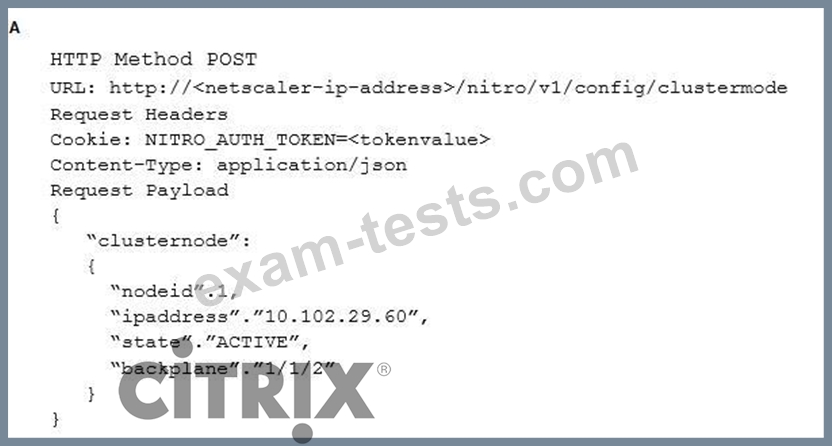
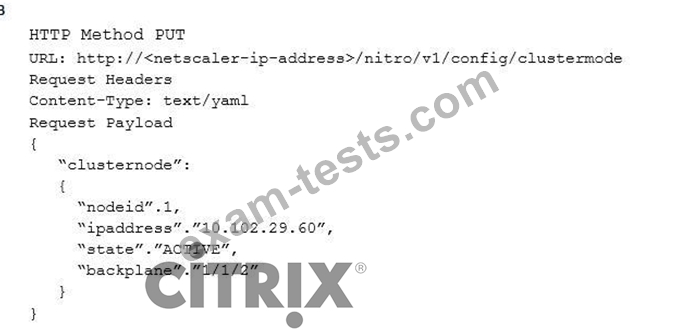
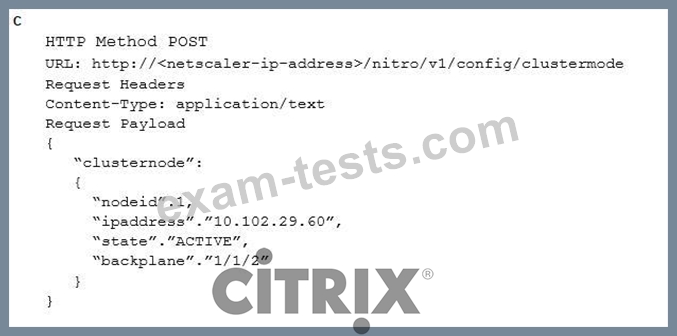
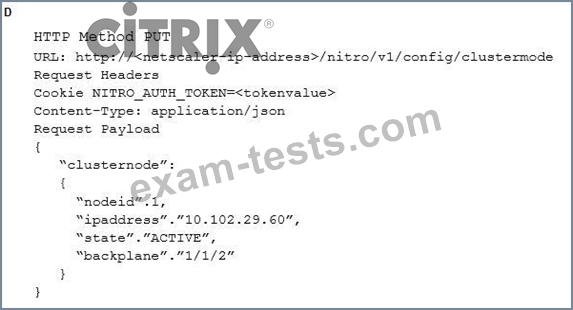




Question 10
Scenario: A Citrix Architect needs to assess an existing NetScaler configuration. The customer recently found that certain user groups were receiving access to an internal web server with an authorization configuration that does NOT align with the designed security requirements.
Click the Exhibit button view the configured authorization settings for the web server.
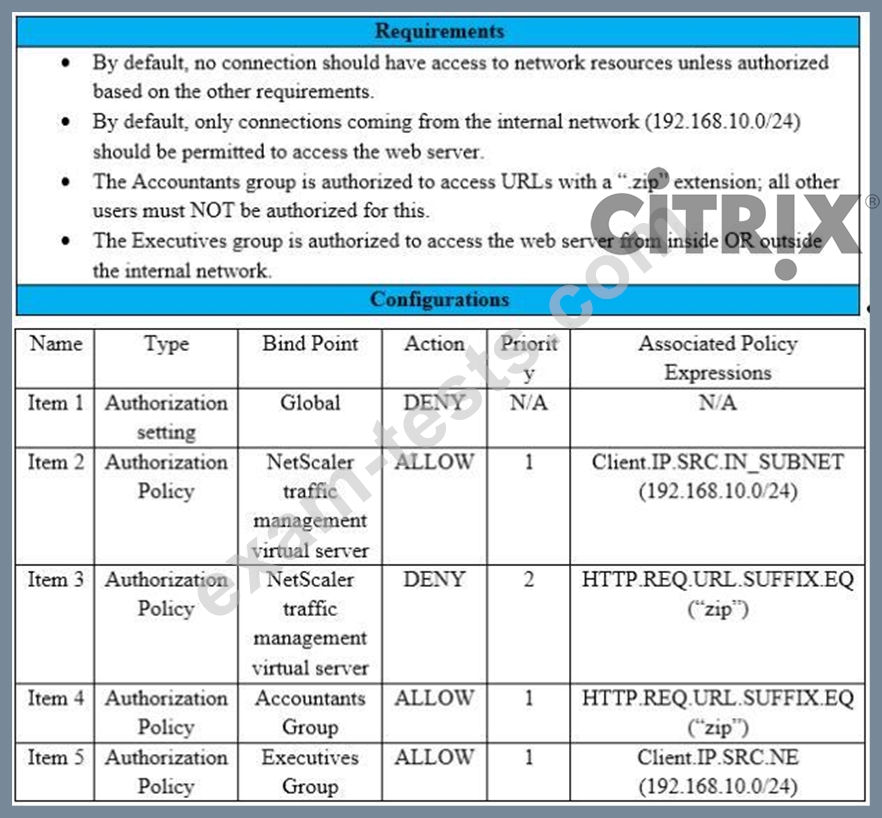
Which item should the architect change or remove to align the authorization configuration with the security requirements of the organization?
Click the Exhibit button view the configured authorization settings for the web server.

Which item should the architect change or remove to align the authorization configuration with the security requirements of the organization?

