Question 21
Scenario: A Citrix Architect needs to assess an existing Citrix ADC configuration. The customer recently found that members of certain administrator groups were receiving permissions on the production Citrix ADC appliances that do NOT align with the designed security requirements. Click the Exhibit button to view the configured command policies for the production Citrix ADC deployment.
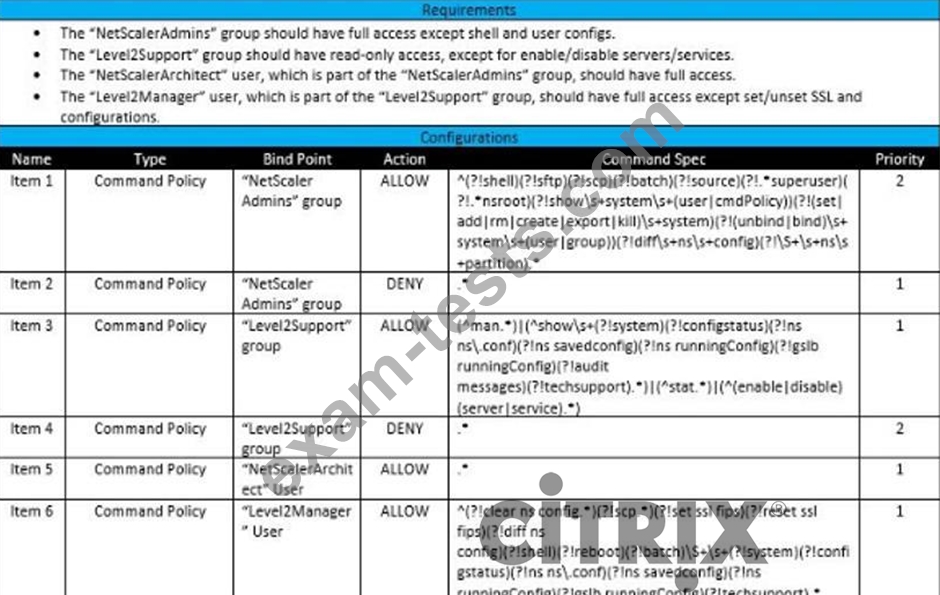
To align the command policy configuration with the security requirements of the organization, the__________for________________should change. (Choose the correct option to complete the sentence.)

To align the command policy configuration with the security requirements of the organization, the__________for________________should change. (Choose the correct option to complete the sentence.)
Question 22
Scenario: A Citrix Architect and a team of Workspacelab members have met for a design discussion about the NetScaler Design Project. They captured the following requirements:
* Two pairs of NetScaler MPX appliances will be deployed in the DMZ network and the internal network.
* High availability will be accessible between the pair of NetScaler MPX appliances in the DMZ network.
* Multi-factor authentication must be configured for the NetScaler Gateway virtual server.
* The NetScaler Gateway virtual server is integrated with XenApp/XenDesktop environment.
* Load balancing must be deployed for the users from the workspacelab.com and vendorlab.com domains.
* The logon page must show the workspacelab logo.
* Certificate verification must be performed to identify and extract the username.
* The client certificate must have UserPrincipalName as a subject.
* All the managed workstations for the workspace users must have a client identifications certificate installed on it.
* The workspacelab users connecting from a managed workstation with a client certificate on it should be authenticated using LDAP.
* The workspacelab users connecting from a workstation without a client certificate should be authenticated using LDAP and RADIUS.
* The vendorlab users should be authenticated using Active Directory Federation Service.
* The user credentials must NOT be shared between workspacelab and vendorlab.
* Single Sign-on must be performed between StoreFront and NetScaler Gateway.
* A domain drop down list must be provided if the user connects to the NetScaler Gateway virtual server externally.
* The domain of the user connecting externally must be identified using the domain selected from the domain drop down list.
On performing the deployment, the architect observes that users are always prompted with two-factor authentication when trying to assess externally from an unmanaged workstation.
Click the exhibit button to view the configuration.
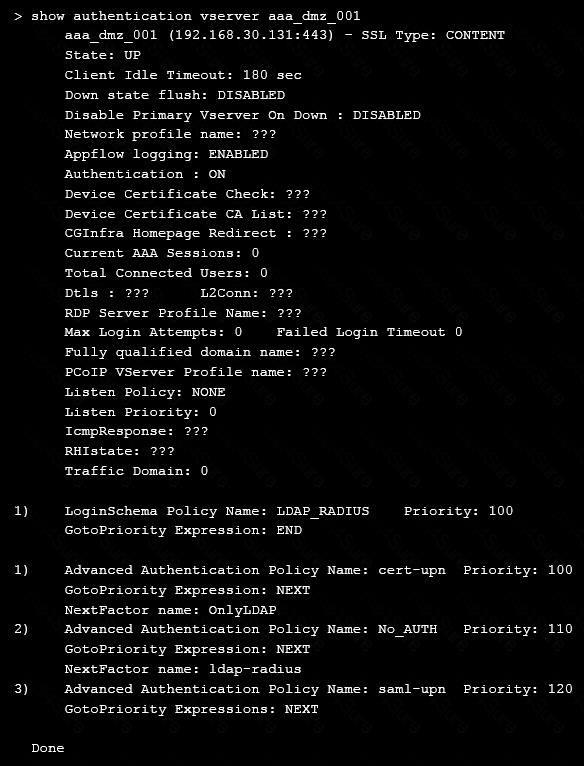
What should the architect do to correct this configuration?
* Two pairs of NetScaler MPX appliances will be deployed in the DMZ network and the internal network.
* High availability will be accessible between the pair of NetScaler MPX appliances in the DMZ network.
* Multi-factor authentication must be configured for the NetScaler Gateway virtual server.
* The NetScaler Gateway virtual server is integrated with XenApp/XenDesktop environment.
* Load balancing must be deployed for the users from the workspacelab.com and vendorlab.com domains.
* The logon page must show the workspacelab logo.
* Certificate verification must be performed to identify and extract the username.
* The client certificate must have UserPrincipalName as a subject.
* All the managed workstations for the workspace users must have a client identifications certificate installed on it.
* The workspacelab users connecting from a managed workstation with a client certificate on it should be authenticated using LDAP.
* The workspacelab users connecting from a workstation without a client certificate should be authenticated using LDAP and RADIUS.
* The vendorlab users should be authenticated using Active Directory Federation Service.
* The user credentials must NOT be shared between workspacelab and vendorlab.
* Single Sign-on must be performed between StoreFront and NetScaler Gateway.
* A domain drop down list must be provided if the user connects to the NetScaler Gateway virtual server externally.
* The domain of the user connecting externally must be identified using the domain selected from the domain drop down list.
On performing the deployment, the architect observes that users are always prompted with two-factor authentication when trying to assess externally from an unmanaged workstation.
Click the exhibit button to view the configuration.

What should the architect do to correct this configuration?
Question 23
Scenario: A Citrix Architect needs to design a hybrid XenApp and XenApp and XenDesktop environment which will include Citrix Cloud as well as resource locations in on-premises datacenter and Microsoft Azure.
Organizational details and requirements are as follows:
* Active XenApp and XenDesktop Service subscription
* No existing NetScaler deployment
* About 3,000 remote users are expected to regularly access the environment
* Multi-factor authentication should be used for all external connections
* Solution must provide load balancing for backend application servers
* Load-balancing services must be in Location B
Click the Exhibit button to view the conceptual environment architecture.
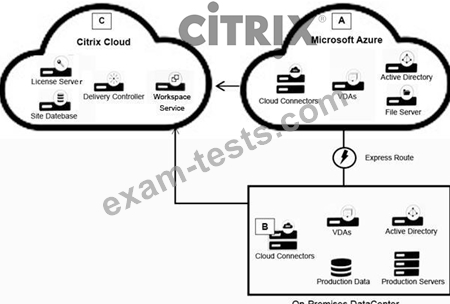
The architect should use ________ in Location A, and should use _________ in Location B.
(Choose the correct option to complete the sentence.)
Organizational details and requirements are as follows:
* Active XenApp and XenDesktop Service subscription
* No existing NetScaler deployment
* About 3,000 remote users are expected to regularly access the environment
* Multi-factor authentication should be used for all external connections
* Solution must provide load balancing for backend application servers
* Load-balancing services must be in Location B
Click the Exhibit button to view the conceptual environment architecture.

The architect should use ________ in Location A, and should use _________ in Location B.
(Choose the correct option to complete the sentence.)
Question 24
Scenario: A Citrix Architect needs to design a new NetScaler Gateway deployment for a customer. During the design discussions, the architect learns that the customer would like to allow external RDP connections to internal Windows machines but does NOT want client drive redirection enabled on these connections.
Where should the architect enable the options to allow the customer to complete their requirement?
Where should the architect enable the options to allow the customer to complete their requirement?
Question 25
Scenario: The Workspacelab team has configured their NetScaler Management and Analytics (NMAS) environment. A Citrix Architect needs to log on to the NMAS to check the settings.
Which two authentication methods are supported to meet this requirement? (Choose two.)
Which two authentication methods are supported to meet this requirement? (Choose two.)

