Question 6
Scenario: A Citrix Architect has set up NetScaler MPX devices in high availability mode with version 12.0.
53.13 nc. These are placed behind a Cisco ASA 5505 Firewall is configured to block traffic using access control lists. The network address translation (NAT) is also performed on the firewall.
The following requirements were captured by the architect during the discussion held as part of the NetScaler security implementation project with the customer's security team:
The NetScaler device:
* Should monitor the rate of traffic either on a specific virtual entity or on the device. It should be able to mitigate the attacks from a hostile client sending a flood of requests. The NetScaler device should be able to stop the HTTP, TCP, and DNS based requests.
* Needs to protect backend servers from overloading.
* Needs to queue all the incoming requests on the virtual server level instead of the service level.
* Should provide access to resources on the basis of priority.
* Should provide protection against well-known Windows exploits, virus-infected personal computers, centrally managed automated botnets, compromised webservers, known spammers/hackers, and phishing proxies.
* Should provide flexibility to enforce the desired level of security check inspections for the requests originating from a specific geolocation database.
* Should block the traffic based on a pre-determined header length, URL length, and cookie length. The device should ensure that characters such as a single straight quote (*); backslash(\), and semicolon (;) are either blocked, transformed, or dropped while being sent to the backend server.
Which two security features should the architect configure to meet these requirements? (Choose two.)
53.13 nc. These are placed behind a Cisco ASA 5505 Firewall is configured to block traffic using access control lists. The network address translation (NAT) is also performed on the firewall.
The following requirements were captured by the architect during the discussion held as part of the NetScaler security implementation project with the customer's security team:
The NetScaler device:
* Should monitor the rate of traffic either on a specific virtual entity or on the device. It should be able to mitigate the attacks from a hostile client sending a flood of requests. The NetScaler device should be able to stop the HTTP, TCP, and DNS based requests.
* Needs to protect backend servers from overloading.
* Needs to queue all the incoming requests on the virtual server level instead of the service level.
* Should provide access to resources on the basis of priority.
* Should provide protection against well-known Windows exploits, virus-infected personal computers, centrally managed automated botnets, compromised webservers, known spammers/hackers, and phishing proxies.
* Should provide flexibility to enforce the desired level of security check inspections for the requests originating from a specific geolocation database.
* Should block the traffic based on a pre-determined header length, URL length, and cookie length. The device should ensure that characters such as a single straight quote (*); backslash(\), and semicolon (;) are either blocked, transformed, or dropped while being sent to the backend server.
Which two security features should the architect configure to meet these requirements? (Choose two.)
Question 7
Which step does a Citrix Architect need to ensure during the Define phase when following the Citrix Methodology?
Question 8
Which parameter must a Citrix Architect configure to ensure that HDX Proxy Connection terminates upon AAA Session TimeOut?
Question 9
Scenario: A Citrix Architect needs to configure a Content Switching virtual server to provide access to www.workspacelab.com. However, the architect observes that whenever the user tries to access www.worksapcelab.com/CITRIX/WEB, the user receives a "503 - Service Unavailable" response. The configuration snippet is as follows:
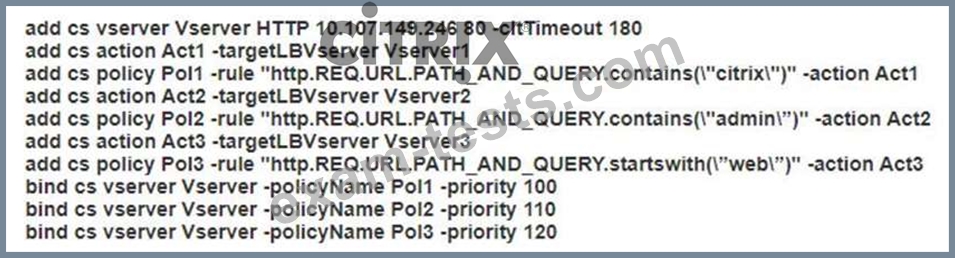
What should the architect modify to resolve this issue?

What should the architect modify to resolve this issue?
Question 10
Scenario: A Citrix Architect needs to assess an existing on-premises NetScaler deployment which includes Advanced Endpoint Analysis scans. During a previous security audit, the team discovered that certain endpoint devices were able to perform unauthorized actions despite NOT meeting pre-established criteria.
The issue was isolated to several endpoint analysis (EPA) scan settings.
Click the Exhibit button to view the endpoint security requirements and configured EPA policy settings.
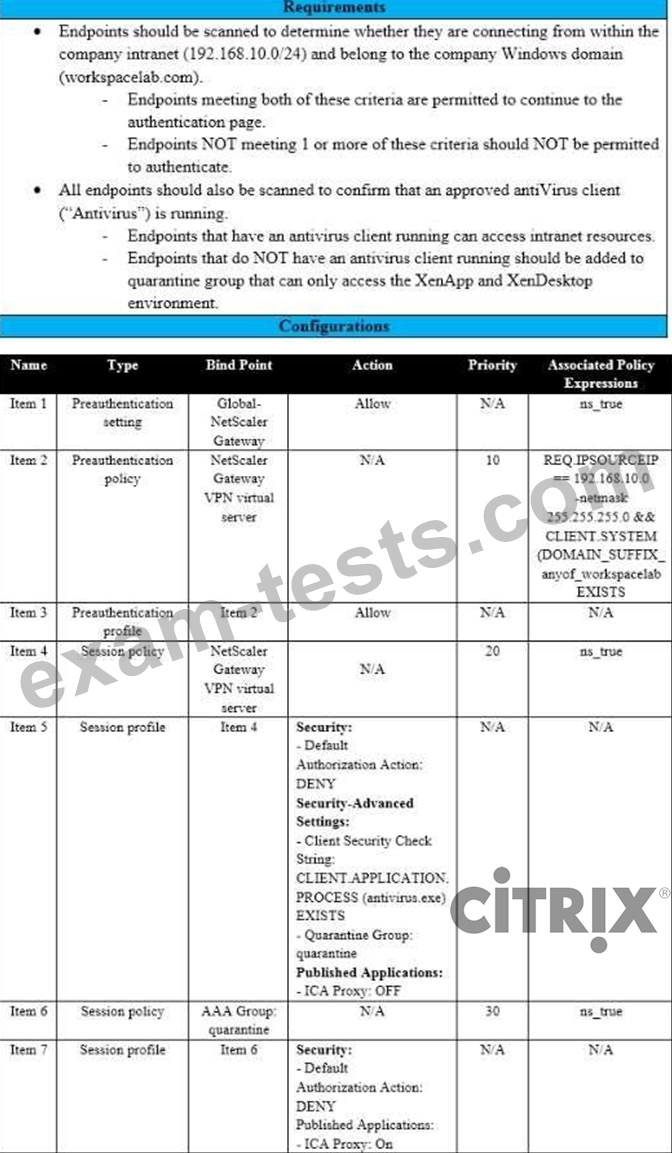
Which setting is preventing the security requirements of the organization from being met?
The issue was isolated to several endpoint analysis (EPA) scan settings.
Click the Exhibit button to view the endpoint security requirements and configured EPA policy settings.

Which setting is preventing the security requirements of the organization from being met?

