Question 46
A security engineer deploys an enterprise-wide host/endpoint technology for all of the company's corporate PCs. Management requests the engineer to block a selected set of applications on all PCs.
Which technology should be used to accomplish this task?
Which technology should be used to accomplish this task?
Question 47
Which security monitoring data type requires the largest storage space?
Question 48
What is personally identifiable information that must be safeguarded from unauthorized access?
Question 49
Refer to the exhibit.
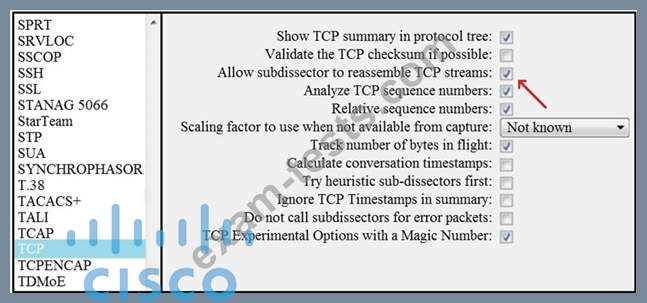
What is the expected result when the "Allow subdissector to reassemble TCP streams" feature is enabled?

What is the expected result when the "Allow subdissector to reassemble TCP streams" feature is enabled?
Question 50
An engineer runs a suspicious file in a sandbox analysis tool to see the outcome. The analysis report shows that outbound callouts were made post infection.
Which two pieces of information from the analysis report are needed to investigate the callouts? (Choose two.)
Which two pieces of information from the analysis report are needed to investigate the callouts? (Choose two.)

