Question 31
Refer to the exhibit.
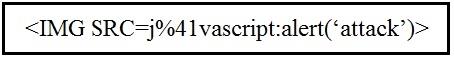
Which kind of attack method is depicted in this string?
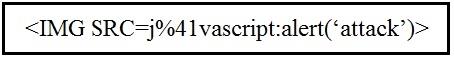
Which kind of attack method is depicted in this string?
Question 32
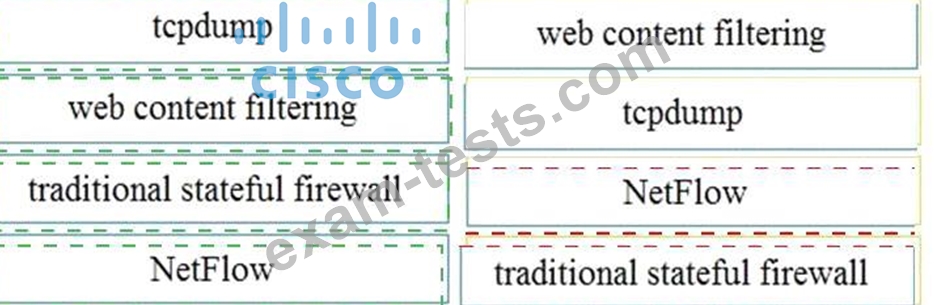
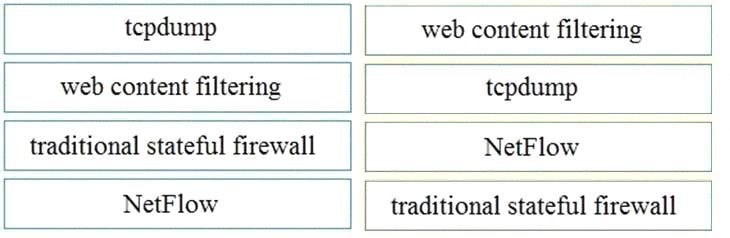
Drag and drop the technology on the left onto the data type the technology provides on the right.


Question 33
How does an attacker observe network traffic exchanged between two users?
Question 34
A security engineer has a video of a suspect entering a data center that was captured on the same day that files in the same data center were transferred to a competitor.
Which type of evidence is this?
Which type of evidence is this?
Question 35
Which attack method intercepts traffic on a switched network?