Question 1
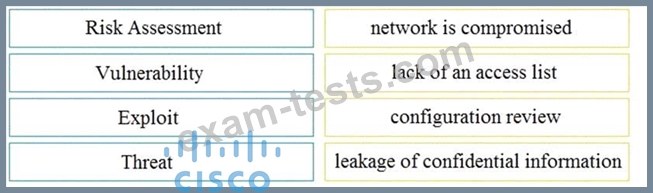
Drag and drop the security concept on the left onto the example of that concept on the right.

Question 2
Refer to the exhibit.
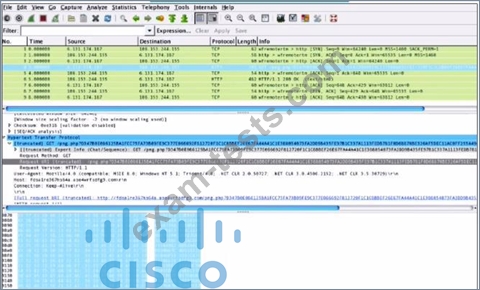
What is shown in this PCAP file?

What is shown in this PCAP file?
Question 3
Which security technology guarantees the integrity and authenticity of all messages transferred to and from a web application?
Question 4
What are two differences in how tampered and untampered disk images affect a security incident? (Choose two.)
Question 5
At which layer is deep packet inspection investigated on a firewall?



