Question 51
An engineer needs to have visibility on TCP bandwidth usage, response time, and latency, combined with deep packet inspection to identify unknown software by its network traffic flow. Which two features of Cisco Application Visibility and Control should the engineer use to accomplish this goal? (Choose two.)
Question 52
Which attack is the network vulnerable to when a stream cipher like RC4 is used twice with the same key?
Question 53
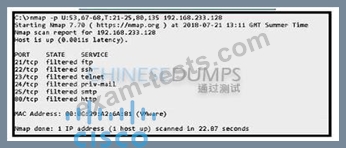
Refer to the exhibit. An attacker scanned the server using Nmap. What did the attacker obtain from this scan?
Question 54
A security expert is working on a copy of the evidence, an ISO file that is saved in CDFS format. Which type of evidence is this file?
Question 55
Which principle is being followed when an analyst gathers information relevant to a security incident to determine the appropriate course of action?

