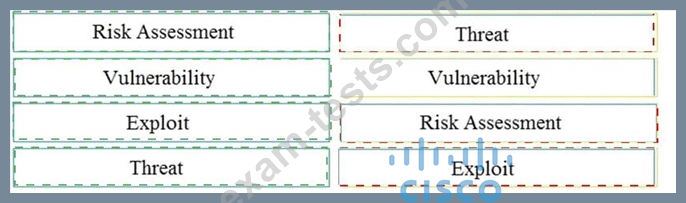
Question 56
Drag and drop the security concept on the left onto the example of that concept on the right.
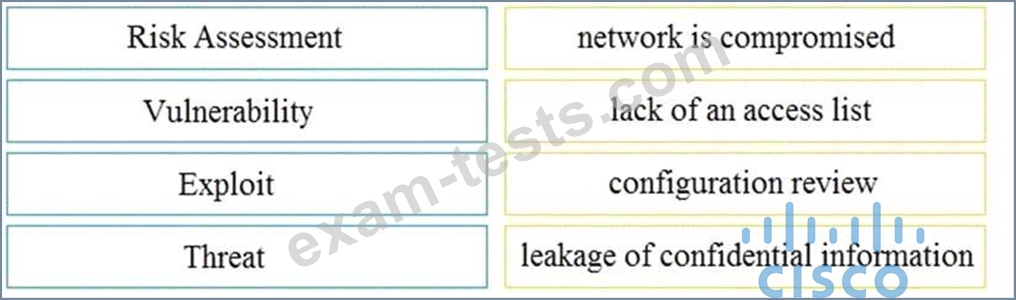

Question 57
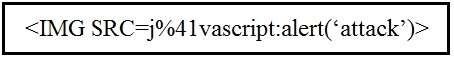
Refer to the exhibit. Which kind of attack method is depicted in this string?
Question 58
A user received a targeted spear-phishing email and identified it as suspicious before opening the content. To which category of the Cyber Kill Chain model does to this type of event belong?
Question 59
Which action should be taken if the system is overwhelmed with alerts when false positives and false negatives are compared?
Question 60
What does an attacker use to determine which network ports are listening on a potential target device?