Question 71
DRAG DROP
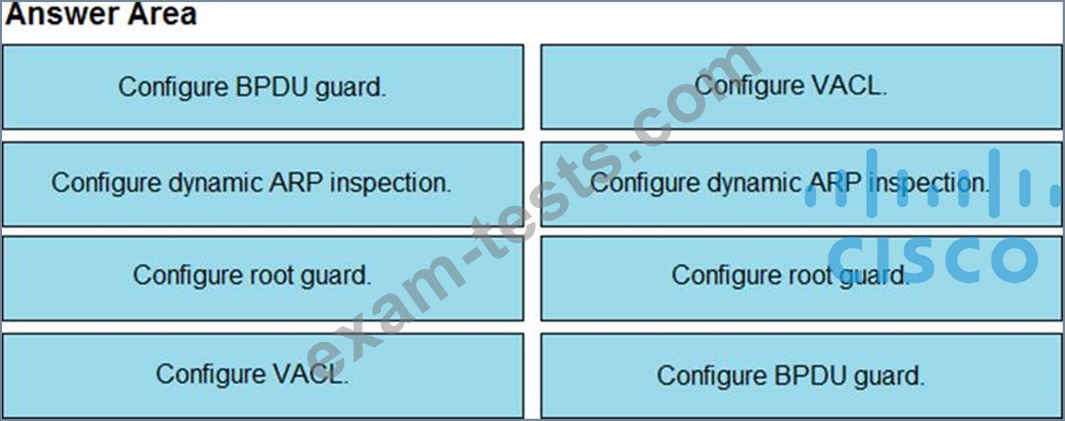
Drag and drop the threat-mitigation techniques from the left onto the types of threat or attack they mitigate on the right.
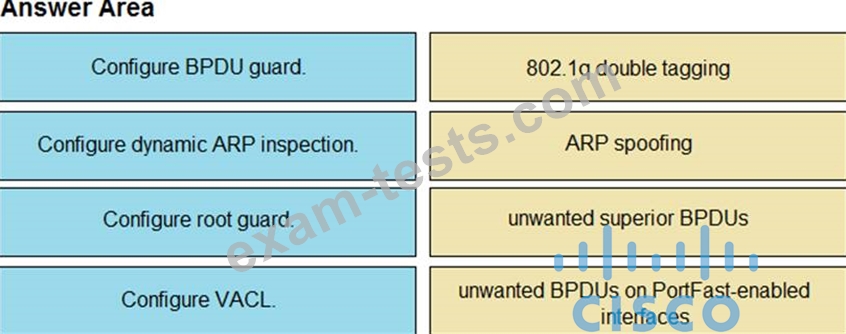
Drag and drop the threat-mitigation techniques from the left onto the types of threat or attack they mitigate on the right.

Question 72
When a WPA2-PSK WLAN is configured in the wireless LAN Controller, what is the minimum number of characters that in ASCll format?
Question 73
What is a function of a remote access VPN?
Question 74
Refer to the exhibit.
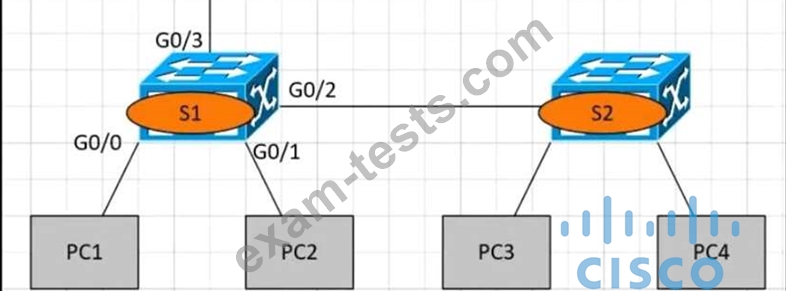
PC1 is trying to ping PC3 for the first time and sends out an ARP to S1 Which action is taken by S1?

PC1 is trying to ping PC3 for the first time and sends out an ARP to S1 Which action is taken by S1?
Question 75
Refer to the exhibit.
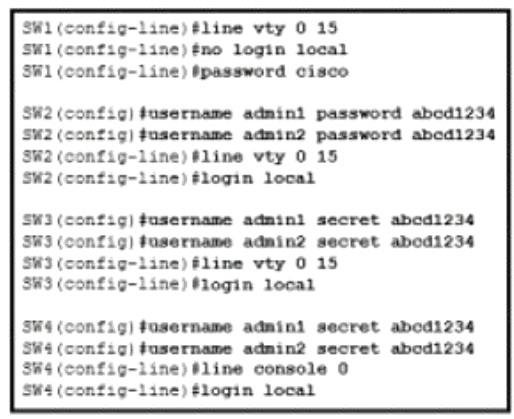
An administrator configures four switches for local authentication using passwords that are stored in a cryptographic hash. The four switches must also support SSH access for administrators to manage the network infrastructure. Which switch is configured correctly to meet these requirements?

An administrator configures four switches for local authentication using passwords that are stored in a cryptographic hash. The four switches must also support SSH access for administrators to manage the network infrastructure. Which switch is configured correctly to meet these requirements?