Question 226
Which action implements physical access control as part of the security program of an organization1?
Question 227
Refer to the exhibit.
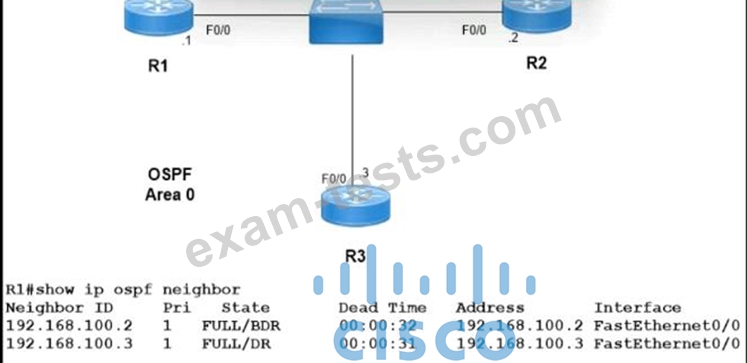
Which two configurations must the engineer apply on this network so that R1 becomes the DR? (Choose two.) A)

B)

C)

D)

E)


Which two configurations must the engineer apply on this network so that R1 becomes the DR? (Choose two.) A)

B)

C)

D)

E)

Question 228
Which syslog severity level is considered the most severe and results in the system being considered unusable?
Question 229
Which two protocols must be disabled to increase security for management connections to a Wireless LAN Controller? (Choose two )
Question 230
How are VLAN hopping attacks mitigated?

