Question 26
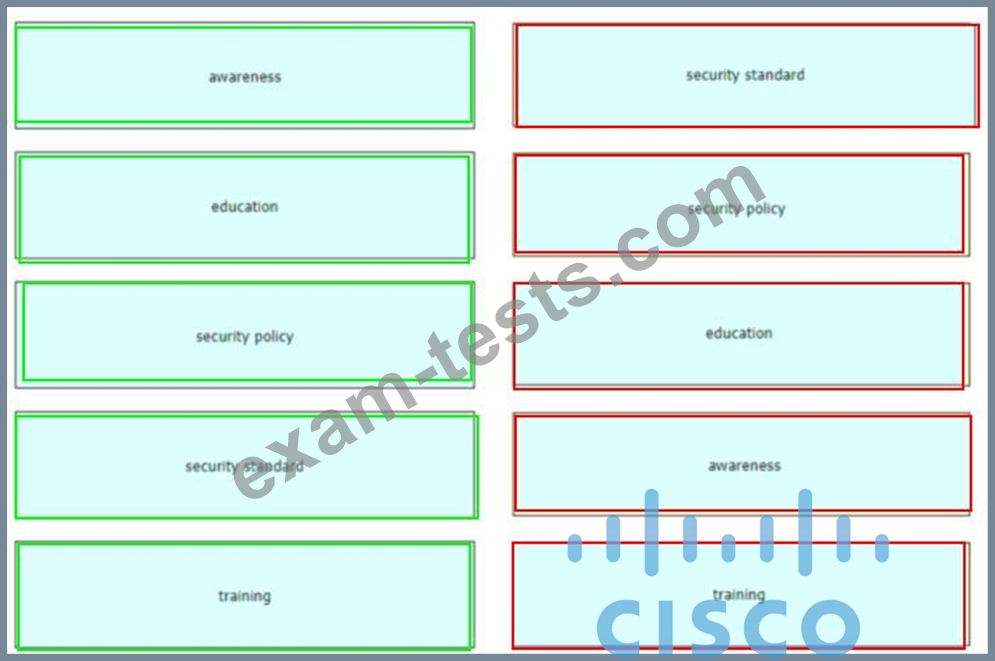
Drag and drop the elements of a security program from the left onto the corresponding descriptions on the right


Question 27
Refer to Exhibit.

Rotor to the exhibit. The IP address configurations must be completed on the DC-1 and HQ-1 routers based on these requirements:
DC-1 Gi1/0 must be the last usable address on a /30
DC-1 Gi1/1 must be the first usable address on a /29
DC-1 Gi1/2 must be the last usable address on a /28
HQ-1 Gil/3 must be the last usable address on a /29
Drag and drop the commands from the left onto the destination interfaces on the right. Not all commands are used
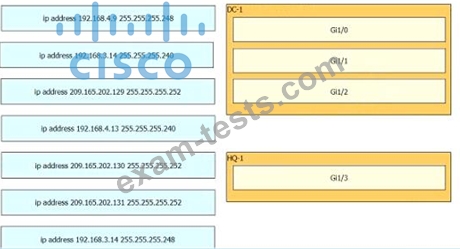

Rotor to the exhibit. The IP address configurations must be completed on the DC-1 and HQ-1 routers based on these requirements:
DC-1 Gi1/0 must be the last usable address on a /30
DC-1 Gi1/1 must be the first usable address on a /29
DC-1 Gi1/2 must be the last usable address on a /28
HQ-1 Gil/3 must be the last usable address on a /29
Drag and drop the commands from the left onto the destination interfaces on the right. Not all commands are used

Question 28
An email user has been lured into clicking a link in an email sent by their company's security organization. The webpage that opens reports that it was safe but the link could have contained malicious code. Which type of security program is in place?
Question 29
Refer to the exhibit.
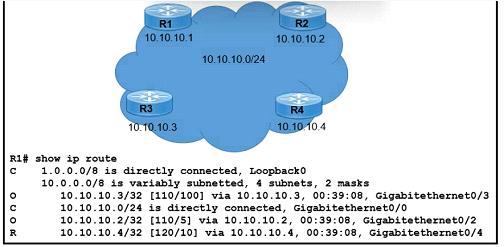
Which next-hop IP address has the least desirable metric when sourced from R1?

Which next-hop IP address has the least desirable metric when sourced from R1?
Question 30
What is the purpose of an SSID?