Question 311
Which action implements physical access control as part of the security program of an organization1?
Question 312
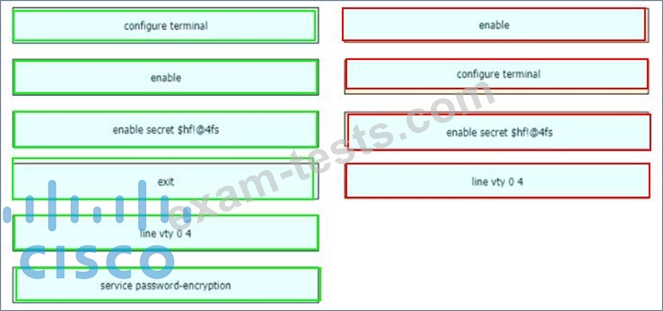
An engineer is configuring an encrypted password for the enable command on a router where the local user database has already been configured Drag and drop the configuration commands from the left into the correct sequence on the right Not all commands are used


Question 313
Refer to the exhibit.

Which action do the switches take on the trunk link?

Which action do the switches take on the trunk link?
Question 314
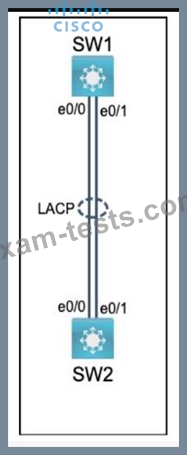
Physical connectivity is implemented between the two Layer 2 switches,
and the network connectivity between them must be configured.
I . Configure an LACP EtherChanneI and number it as 44; configure it
between switches SWI and SW2 using interfaces EthernetO/O and
Ethernet0/1 on both sides. The LACP mode must match on both ends.
2. Configure the EtherChanneI as a trunk link.
3. Configure the trunk link with 802. Iq tags.
4. Configure VLAN 'MONITORING' as the untagged VLAN of the
EtherChannel.
Guidelines
This is a lab item in which tasks will be performed on virtual devices.
* Refer to the Tasks tab to view the tasks for this lab item.
* Refer to the Topology tab to access the device console(s) and perform the tasks.
* Console access is available for all required devices by clicking the device icon or using
the tab(s) above the console window.
* All necessary preconfigurations have been applied.
* Do not change the enable password or hostname for any device.
* Save your configurations to NVRAM before moving to the next item.
* Click Next at the bottom of the screen to submit this lab and move to the next question.
* When Next is clicked, the lab closes and cannot be reopened.
and the network connectivity between them must be configured.
I . Configure an LACP EtherChanneI and number it as 44; configure it
between switches SWI and SW2 using interfaces EthernetO/O and
Ethernet0/1 on both sides. The LACP mode must match on both ends.
2. Configure the EtherChanneI as a trunk link.
3. Configure the trunk link with 802. Iq tags.
4. Configure VLAN 'MONITORING' as the untagged VLAN of the
EtherChannel.
Guidelines
This is a lab item in which tasks will be performed on virtual devices.
* Refer to the Tasks tab to view the tasks for this lab item.
* Refer to the Topology tab to access the device console(s) and perform the tasks.
* Console access is available for all required devices by clicking the device icon or using
the tab(s) above the console window.
* All necessary preconfigurations have been applied.
* Do not change the enable password or hostname for any device.
* Save your configurations to NVRAM before moving to the next item.
* Click Next at the bottom of the screen to submit this lab and move to the next question.
* When Next is clicked, the lab closes and cannot be reopened.

Question 315
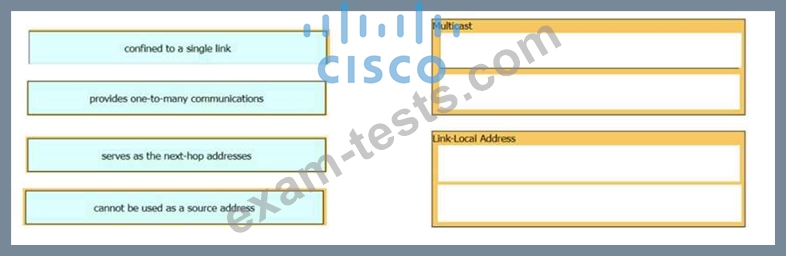
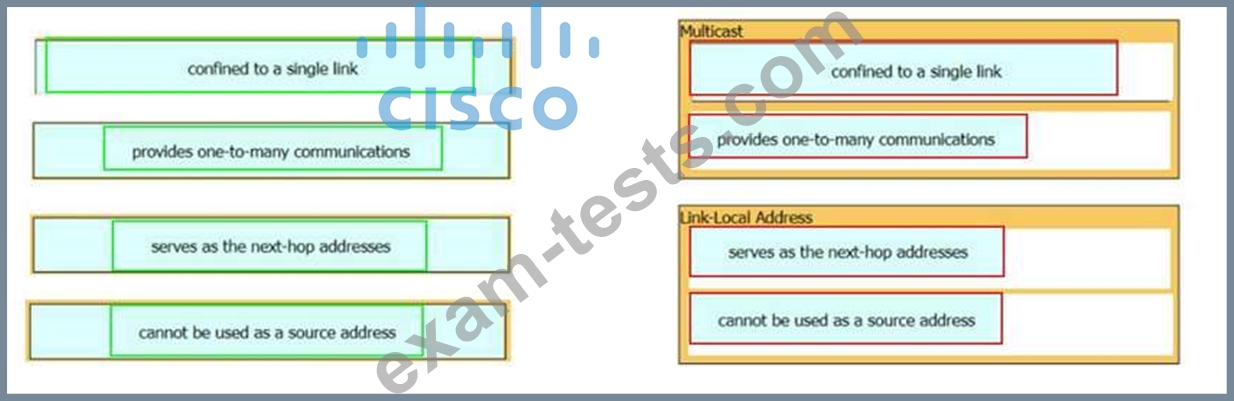
Drag and drop the characteristic from the left onto the IPv6 address type on the right.