Question 141
SIMULATION
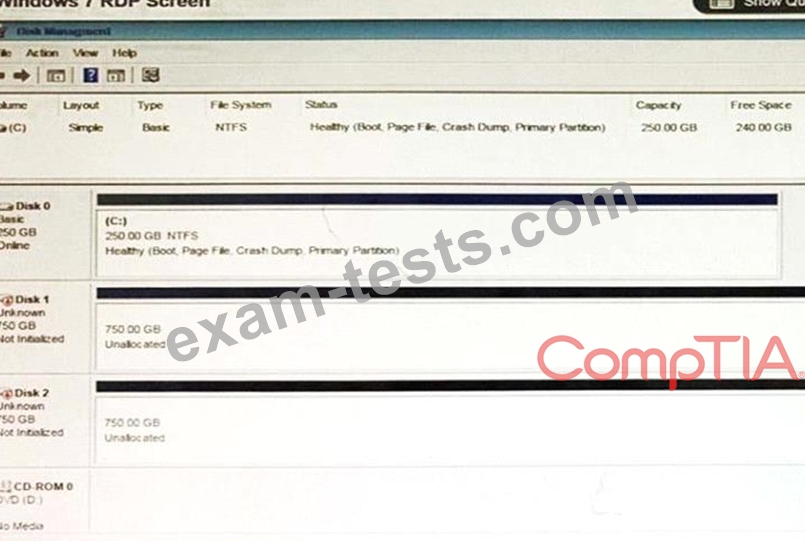
A user has installed two new drives in one of the computers in the computer lab and has been unable to format Disk1 from the command prompt.
The lab requires that Disk1 be a dynamic disk configured with two partitions. The first partition must be 256,000 MB in size and mapped to drive F.
The second partition must be 512,000 MB in size and mapped to drive G.
The new partitions must be formatted to ensure that user's files can be secured from other users and that the disk must be configured to account for future redundancy.
Make sure to maintain a consistent file system.
INSTRUCTIONS:
Conduct the necessary steps within the Disk Manager to accomplish these tasks.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
A user has installed two new drives in one of the computers in the computer lab and has been unable to format Disk1 from the command prompt.
The lab requires that Disk1 be a dynamic disk configured with two partitions. The first partition must be 256,000 MB in size and mapped to drive F.
The second partition must be 512,000 MB in size and mapped to drive G.
The new partitions must be formatted to ensure that user's files can be secured from other users and that the disk must be configured to account for future redundancy.
Make sure to maintain a consistent file system.
INSTRUCTIONS:
Conduct the necessary steps within the Disk Manager to accomplish these tasks.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.

Question 142
The management team has issued a new directive that states a certain string is no longer allowed in any of the names on any of the Linux workstation. Which of the following commands would a technician issue to find all the instances of the unwanted string on a workstation?
Question 143
Following an incident, an administrator is gathering forensic evidence from a server for a human resources investigation. Which of the following best practices is MOST important to document throughout the process to maintain integrity of the findings?
Question 144
An employee reported that a suspicious individual was looking through the recycle bin.
Which of the following types of social engineering threats is this?
Which of the following types of social engineering threats is this?
Question 145
A technician responds to a call from a user who claims to have a virus on a workstation. The technician observes the following notification from the system tray:
There are 1033 infected files on this computer. Click here to disinfect.
The link is blocked by the corporate content filter and displays a message stating the site contains known malware. Which of the following should the technician complete to secure the computer with MINIMAL impact to the user?
There are 1033 infected files on this computer. Click here to disinfect.
The link is blocked by the corporate content filter and displays a message stating the site contains known malware. Which of the following should the technician complete to secure the computer with MINIMAL impact to the user?

