Question 46
Which two choices are use cases for Distributed Intrusion Detection? (Choose two.)
Question 47
An administrator needs to encrypt file transfers between two sites that do not have the same subnet. Which NSX-T feature accomplishes this task?
Question 48
An administrator wants to validate the BGP connection status between the Tier-0 Gateway and the upstream physical router.
What sequence of commands could be used to check this status on NSX Edge node?
What sequence of commands could be used to check this status on NSX Edge node?
Question 49
Which two commands does an NSX administrator use to check the IP address of the VMkernel port for the Geneve protocol on the ESXi transport node? (Choose two.)
Question 50
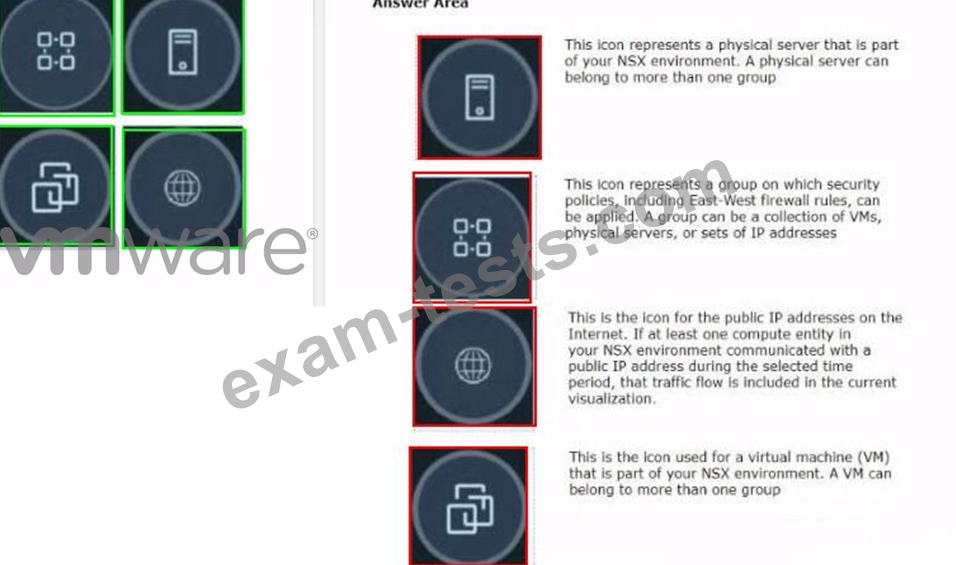
Refer to the exhibits.
Drag and drop the NSX graphic element icons on the left found in an NSX Intelligence visualization graph to Its correct description on the right.

Drag and drop the NSX graphic element icons on the left found in an NSX Intelligence visualization graph to Its correct description on the right.