Question 96
While searching through a computer under investigation, you discover numerous files that appear to have had the first letter of the file name replaced by the hex code byte 5h.?What does this indicate on the computer?replaced by the hex code byte ?5h.?What does this indicate on the computer?
Question 97
The following is a log file screenshot from a default installation of IIS 6.0.
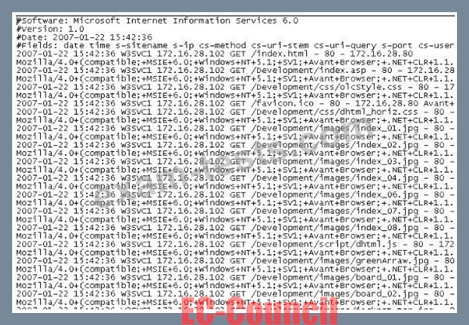
What time standard is used by IIS as seen in the screenshot?

What time standard is used by IIS as seen in the screenshot?
Question 98
Company ABC has employed a firewall, IDS, Antivirus, Domain Controller, and SIEM. The company's domain controller goes down. From which system would you begin your investigation?
Question 99
You are called in to assist the police in an investigation involving a suspected drug dealer.
The police searched the suspect house after aYou are called in to assist the police in an investigation involving a suspected drug dealer. The police searched the suspect? house after a warrant was obtained and they located a floppy disk in the suspect bedroom. The disk contains several files, but they appear to be passwordwarrant was obtained and they located a floppy disk in the suspect? bedroom. The disk contains several files, but they appear to be password protected. What are two common methods used by password cracking software that you could use to obtain the password?
The police searched the suspect house after aYou are called in to assist the police in an investigation involving a suspected drug dealer. The police searched the suspect? house after a warrant was obtained and they located a floppy disk in the suspect bedroom. The disk contains several files, but they appear to be passwordwarrant was obtained and they located a floppy disk in the suspect? bedroom. The disk contains several files, but they appear to be password protected. What are two common methods used by password cracking software that you could use to obtain the password?
Question 100
Which table is used to convert huge word lists (i .e. dictionary files and brute-force lists) into password hashes?

