Question 281
Tremp is an IT Security Manager, and he is planning to deploy an IDS in his small company. He is looking
for an IDS with the following characteristics: -Verifies success or failure of an attack - Monitors system
activities - Detects attacks that a network-based IDS fails to detect. - Near real-time detection and
response - Does not require additional hardware - Lower entry cost. Which type of IDS is best suited for
Tremp's requirements?
for an IDS with the following characteristics: -Verifies success or failure of an attack - Monitors system
activities - Detects attacks that a network-based IDS fails to detect. - Near real-time detection and
response - Does not require additional hardware - Lower entry cost. Which type of IDS is best suited for
Tremp's requirements?
Question 282
An incident investigator asks to receive a copy of the event logs from all firewalls, proxy servers, and Intrusion Detection Systems (IDS) on the network of an organization that has experienced a possible breach of security.
When the investigator attempts to correlate the information in all of the logs, the sequence of many of the logged events do not match up.
What is the most likely cause?
When the investigator attempts to correlate the information in all of the logs, the sequence of many of the logged events do not match up.
What is the most likely cause?
Question 283
A network security administrator is worried about potential man-in-the-middle attacks when users access a corporate web site from their workstations. Which of the following is the best remediation against this type of attack?
Question 284
The security administrator of ABC needs to permit Internet traffic in the host 10.0.0.2 and UDP traffic in the host 10.0.0.3. He also needs to permit all FTP traffic to the rest of the network and deny all other traffic. After he applied his ACL configuration in the router, nobody can access to the ftp, and the permitted hosts cannot access the Internet. According to the next configuration, what is happening in the network?
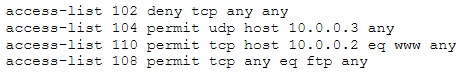

Question 285
A hacker is an intelligent individual with excellent computer skills and the ability to explore a computer's software and hardware without the owner's permission. Their intention can either be to simply gain knowledge or to illegally make changes. Which of the following class of hacker refers to an individual who works both offensively and defensively at various times?

