Question 286
An incident investigator asks to receive a copy of the event logs from all firewalls, proxy servers, and
Intrusion Detection Systems (IDS) on the network of an organization that has experienced a possible
breach of security. When the investigator attempts to correlate the information in all of the logs, the
sequence of many of the logged events do not match up.
What is the most likely cause?
Intrusion Detection Systems (IDS) on the network of an organization that has experienced a possible
breach of security. When the investigator attempts to correlate the information in all of the logs, the
sequence of many of the logged events do not match up.
What is the most likely cause?
Question 287
Switches maintain a CAM Table that maps individual MAC addresses on the network to physical ports on the switch.
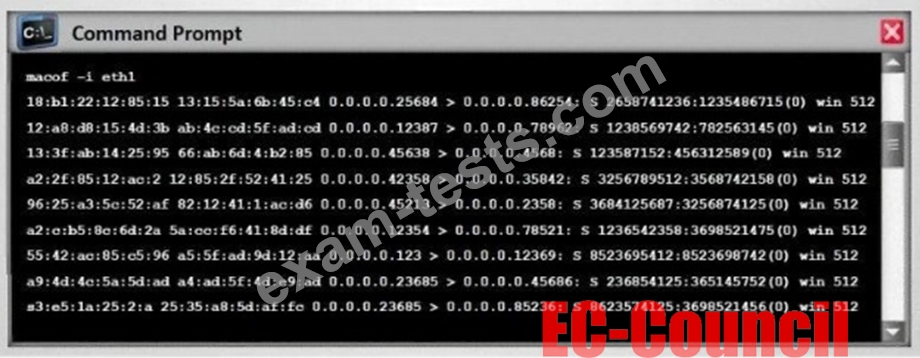
In MAC flooding attack, a switch is fed with many Ethernet frames, each containing different source MAC addresses, by the attacker. Switches have a limited memory for mapping various MAC addresses to physical ports. What happens when the CAM table becomes full?

In MAC flooding attack, a switch is fed with many Ethernet frames, each containing different source MAC addresses, by the attacker. Switches have a limited memory for mapping various MAC addresses to physical ports. What happens when the CAM table becomes full?
Question 288
In both pharming and phishing attacks an attacker can create websites that look similar to legitimate sites with the intent of collecting personal identifiable information from its victims. What is the difference between pharming and phishing attacks?
Question 289
You are monitoring the network of your organizations. You notice that:
Which of the following solution will you suggest?
Which of the following solution will you suggest?
Question 290
Which mode of IPSec should you use to assure security and confidentiality of data within the same LAN?

