Question 36
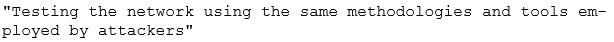
Identify the correct terminology that defines the above statement.
Question 37
Bluetooth uses which digital modulation technique to exchange information between paired devices?
Question 38
What is the main reason the use of a stored biometric is vulnerable to an attack?
Question 39
A penetration tester is conducting a port scan on a specific host. The tester found several ports opened that were confusing in concluding the Operating System (OS) version installed. Considering the NMAP result below, which of the following is likely to be installed on the target machine by the OS?


Question 40
It is a short-range wireless communication technology intended to replace the cables connecting portable of fixed devices while maintaining high levels of security. It allows mobile phones, computers and other devices to connect and communicate using a short-range wireless connection.
Which of the following terms best matches the definition?
Which of the following terms best matches the definition?

