Question 31
A hacker is attempting to use nslookup to query Domain Name Service (DNS). The hacker uses the nslookup interactive mode for the search. Which command should the hacker type into the command shell to request the appropriate records?
Question 32
Which results will be returned with the following Google search query? site:target.com site:Marketing.target.com accounting
Question 33
The following is part of a log file taken from the machine on the network with the IP address of
192.168.1.106:
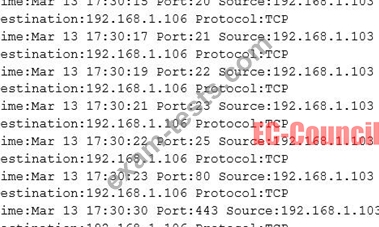
What type of activity has been logged?
192.168.1.106:

What type of activity has been logged?
Question 34
What term describes the amount of risk that remains after the vulnerabilities are classified and the countermeasures have been deployed?
Question 35
ViruXine.W32 virus hides their presence by changing the underlying executable code.
This Virus code mutates while keeping the original algorithm intact, the code changes itself each time it runs, but the function of the code (its semantics) will not change at all.
Here is a section of the Virus code:
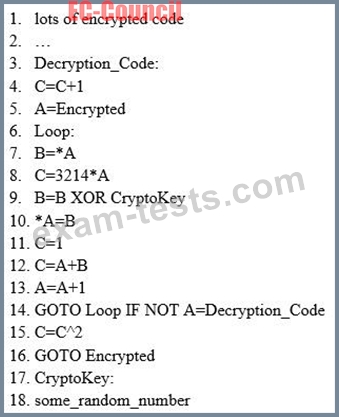
What is this technique called?
This Virus code mutates while keeping the original algorithm intact, the code changes itself each time it runs, but the function of the code (its semantics) will not change at all.

Here is a section of the Virus code:

What is this technique called?

