Question 21
Consider the following Nmap output:
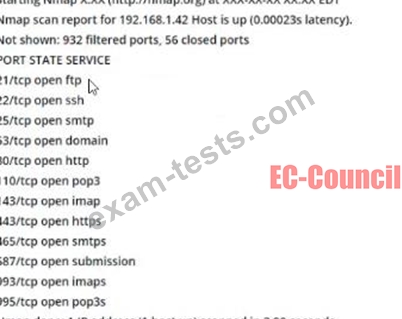
what command-line parameter could you use to determine the type and version number of the web server?

what command-line parameter could you use to determine the type and version number of the web server?
Question 22
John, a professional hacker, targeted an organization that uses LDAP for accessing distributed directory services. He used an automated tool to anonymously query the IDAP service for sensitive information such as usernames. addresses, departmental details, and server names to launch further attacks on the target organization.
What is the tool employed by John to gather information from the IDAP service?
What is the tool employed by John to gather information from the IDAP service?
Question 23
Which of the following is assured by the use of a hash?
Question 24
While scanning with Nmap, Patin found several hosts which have the IP ID of incremental sequences. He then decided to conduct: nmap -Pn -p- -si kiosk.adobe.com www.riaa.com. kiosk.adobe.com is the host with incremental IP ID sequence. What is the purpose of using "-si" with Nmap?
Question 25
Study the snort rule given below:

From the options below, choose the exploit against which this rule applies.

From the options below, choose the exploit against which this rule applies.

