Question 46
Which of the following security procedures is NOT related to the SDLC's disposition?
Question 47
Which of the following terms refers to a programming pattern in which computers are clustered together in a distributed and parallel fashion?
Question 48
A company wants to implement a data backup method that allows them to encrypt the data ensuring its security as well as access at any time and from any location. What is the appropriate backup method that should be implemented?
Question 49
Drag and Drop Question
Choose the steps involved in the general disaster recovery procedure.
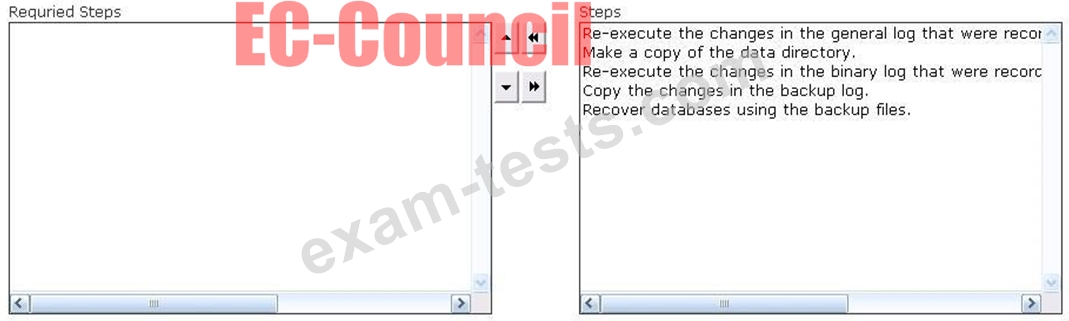
Choose the steps involved in the general disaster recovery procedure.

Question 50
BS 7799 is an internationally recognized ISM standard that provides high level, conceptual recommendations on enterprise security. BS 7799 is basically divided into three parts. Which of the following statements are true about BS 7799?
Each correct answer represents a complete solution. Choose all that apply.
Each correct answer represents a complete solution. Choose all that apply.

