Question 61
Which of the following is NOT a component of a centralized governance structure for Business Continuity and Risk Management?
Question 62
Which of the following is the simulation of the disaster recovery plans?
Question 63
Allen works as a professional Computer Hacking Forensic Investigator. A project has been assigned to him to investigate a computer, which is used by the suspect to sexually harass the victim using instant messenger program. Suspect's computer runs on Windows operating system.
Allen wants to recover password from instant messenger program, which suspect is using, to collect the evidence of the crime. Allen is using Helix Live for this purpose. Which of the following utilities of Helix will he use to accomplish the task?
Allen wants to recover password from instant messenger program, which suspect is using, to collect the evidence of the crime. Allen is using Helix Live for this purpose. Which of the following utilities of Helix will he use to accomplish the task?
Question 64
Which of the following ensures that the confidentiality, integrity, and availability of the services are maintained to the levels approved on the Service Level Agreement (SLA)?
Question 65
Drag and Drop Question
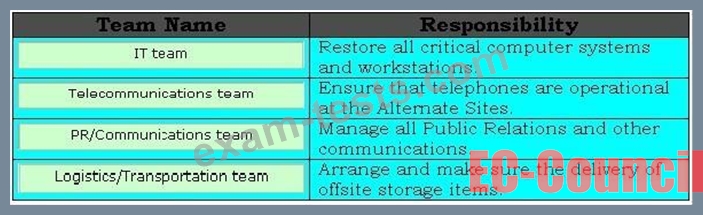
Drag and drop the appropriate team names in front of their respective responsibilities.
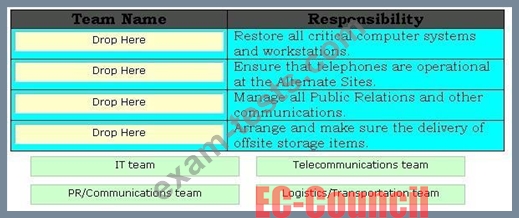
Drag and drop the appropriate team names in front of their respective responsibilities.