Question 91
In risk analysis, which of the following can be identified as a consequence of a disaster?
Question 92
You work as a senior project manager in SoftTech Inc. You are working on a software project using configuration management. Through configuration management, you are decomposing the verification system into identifiable, understandable, manageable, traceable units that are known as Configuration Items (CIs). According to you, which of the following processes is known as the decomposition process of a verification system into Configuration Items?
Question 93
Drag and Drop Questions
Disaster recovery plan consists of various tiers for identifying the methods of recovering mission- critical computer systems that are necessary to support business continuity. All these tiers provide a simple method to define current service levels and associated risks. Choose and re- order the tiers of disaster recovery plan.
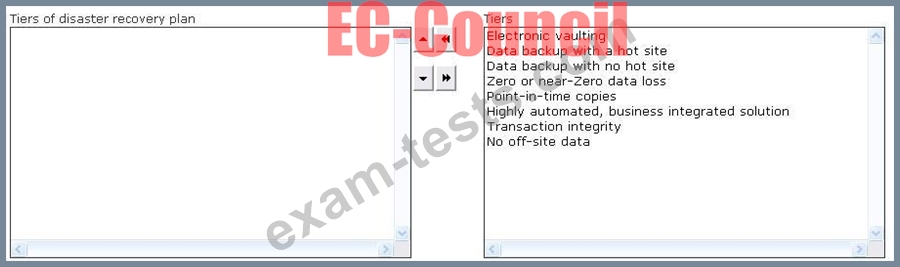
Disaster recovery plan consists of various tiers for identifying the methods of recovering mission- critical computer systems that are necessary to support business continuity. All these tiers provide a simple method to define current service levels and associated risks. Choose and re- order the tiers of disaster recovery plan.

Question 94
Against which of the following does SSH provide protection?
Each correct answer represents a complete solution. Choose two.
Each correct answer represents a complete solution. Choose two.
Question 95
Which of the following processes is used by organizations to set the risk tolerance, identify the potential risks, and prioritize the tolerance for risk?

