Question 186
Which algorithm provides encryption and authentication for data plane communication?
Question 187
An attacker needs to perform reconnaissance on a target system to help gain access to it. The system has weak passwords, no encryption on the VPN links, and software bugs on the system's applications. Which vulnerability allows the attacker to see the passwords being transmitted in clear text?
Question 188
Which two probes are configured to gather attributes of connected endpoints using Cisco Identity Services Engine? (Choose two.)
Question 189
What is a benefit of using telemetry over SNMP to configure new routers for monitoring purposes?
Question 190
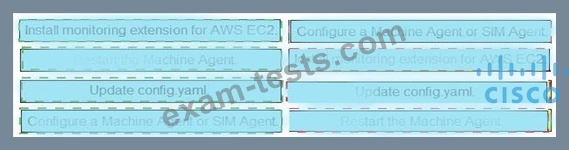
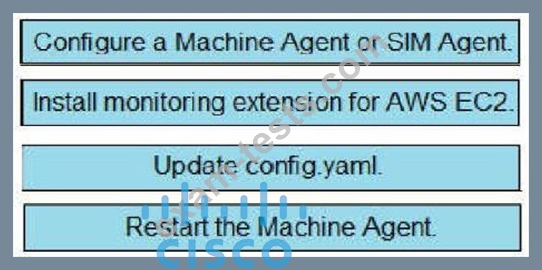
Drag and drop the steps from the left into the correct order on the right to enable AppDynamics to monitor an EC2 instance in Amazon Web Services.