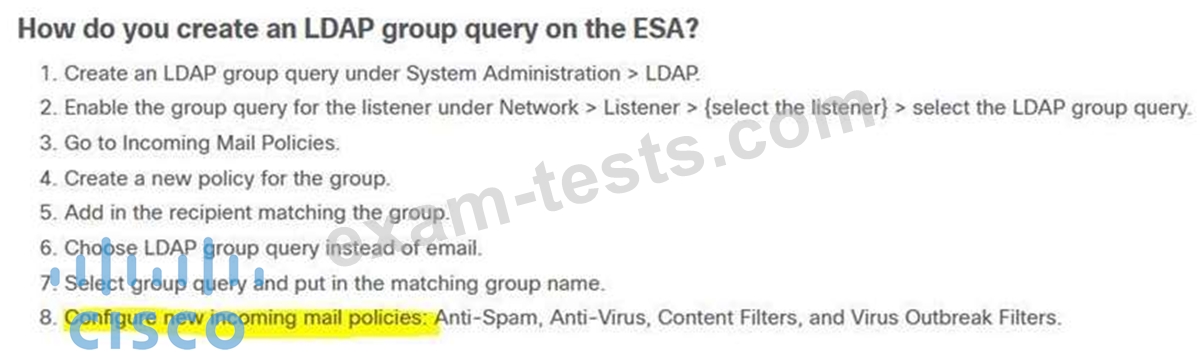
Question 201
When Cisco and other industry organizations publish and inform users of known security findings and vulnerabilities, which name is used?
Question 202
Which attack is commonly associated with C and C++ programming languages?
Question 203
An engineer has enabled LDAP accept queries on a listener. Malicious actors must be prevented from quickly identifying all valid recipients. What must be done on the Cisco ESA to accomplish this goal?
Question 204
What features does Cisco FTDv provide over ASAv?