Question 231
Refer to the exhibit.
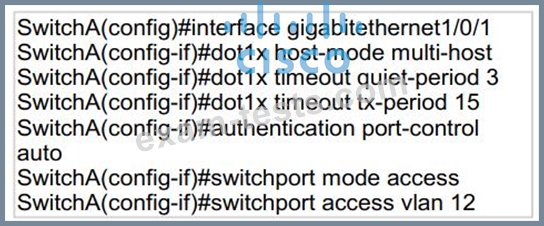
An engineer configured wired 802.1x on the network and is unable to get a laptop to authenticate. Which port configuration is missing?

An engineer configured wired 802.1x on the network and is unable to get a laptop to authenticate. Which port configuration is missing?
Question 232
Which two key and block sizes are valid for AES? (Choose two.)
Question 233
In an IaaS cloud services model, which security function is the provider responsible for managing?
Question 234
In which two ways does a system administrator send web traffic transparently to the Web Security Appliance? (Choose two.)
Question 235
Which two methods must be used to add switches into the fabric so that administrators can control how switches are added into DCNM for private cloud management? (Choose two.)

