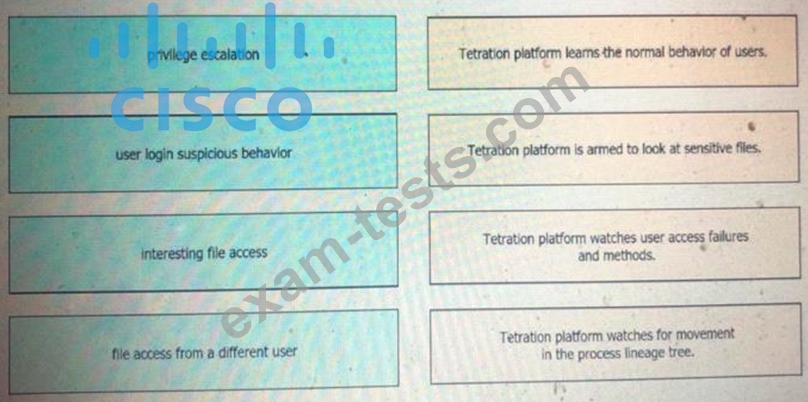
Question 111
Drag and drop the suspicious patterns for the Cisco Tetration platform from the left onto the correct definitions on the right.

Question 112
An attacker needs to perform reconnaissance on a target system to help gain access to it. The system has weak passwords, no encryption on the VPN links, and software bugs on the system's applications. Which vulnerability allows the attacker to see the passwords being transmitted in clear text?
Question 113
Refer to the exhibit.
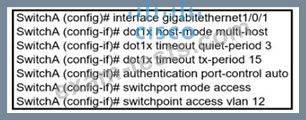
An engineer configured wired 802.1x on the network and is unable to get a laptop to authenticate. Which port configuration is missing?

An engineer configured wired 802.1x on the network and is unable to get a laptop to authenticate. Which port configuration is missing?
Question 114
A network engineer has entered the snmp-server user andy myv3 auth sha cisco priv aes 256 cisc0383320506 command and needs to send SNMP information to a host at 10.255.254.1. Which command achieves this goal?
Question 115
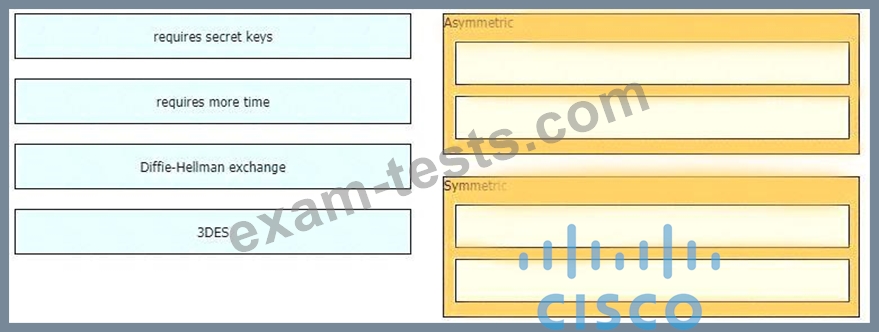
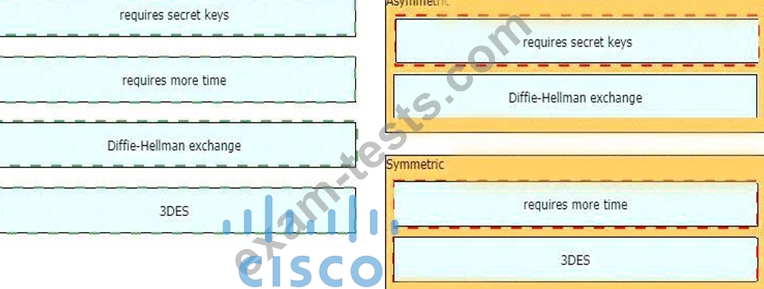
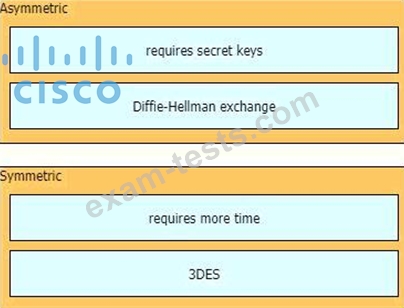
Drag and drop the descriptions from the left onto the encryption algorithms on the right.